The CHEQ Up | Vol. 1 | The Bot Beneath the Banner
Jamie Vinkle
|Privacy & Compliance | June 12, 2025

Welcome to the CHEQ Up
Your new trusted resource in navigating the complex intersection of data security, privacy, and digital engagement. In this inaugural post, we dive directly into one of the most revealing incidents in recent memory—the enforcement action against Google by the state of Texas—and explore why it demonstrates that toggles, checkboxes, and settings alone can never truly safeguard our digital lives.
Trusting the Toggles
Recently, Texas brought forward an enforcement action against Google, alleging serious violations related to deceptive tracking and data privacy. Despite users clearly opting out through various toggles and settings provided by Google, the state argued that Google continued tracking and collecting personal identifiable information (PII) without consent. Google’s case underscores a disturbing reality: relying purely on provided controls means trusting someone else—often the same entities benefiting from data collection—to respect and enforce those boundaries. For businesses this is a high stakes gamble. If you are relying on Google, or Meta, or anyone outside your own organization, you have ceded control.
This case isn’t an isolated incident. It highlights a persistent, industry-wide issue: users and businesses alike mistakenly believe that enabling privacy toggles is sufficient. However, the Google scenario makes clear that toggles and privacy settings alone are insufficient barriers against invasive data practices.
Moving Beyond Cookie Obsession
Today’s digital privacy conversation is often fixated on cookies—so much so that regulators, companies, and end-users alike pour immense resources into banners, pop-ups, and policy fine print. But this focus is misplaced. Cookies that aren’t carried with requests or don’t transmit data to third parties pose little to no real threat. Like a tree falling in the forest with no one around—if it even does. By obsessing over cookies alone, we overlook far more critical vulnerabilities in the digital ecosystem: invalid traffic, bot activity, and risks introduced by third-party technologies. These are the real sources of data loss and compliance failures—not a passive cookie sitting idle in a browser.
Don’t get me wrong, you need a banner to collect preferences and cookies surely play a role in all of this. This should be the starting point, not the pinnacle of compliance. Approved technologies often scoop up PII or PHI by mistake. Anyone with a session replay tool on their site has probably done this. Partners place their own technologies on your site with the best of intentions and leave you exposed to their privacy posture in addition to your own. Compliance gaps you didn’t even know existed hiding in an innocent Floodlight tag from your agency. Add to that all the chat interfaces marketing and customer support added to the site to improve efficiency. They did that by connecting a prompting interface from your digital properties to your internal data. Hello bots and AI! I hope you have real good guard rails against data exfiltration.
You get the idea. Cookies aren’t so bad at the end of the day. Let’s stop misplacing our focus.
The AI Bot Threat: Unseen but not Unfelt
The explosion of AI technology has opened new frontiers in digital threats, particularly concerning malicious traffic. Bots run by bad actors now execute highly sophisticated attacks, ranging from scraping PII out of forms and URL parameters to the dystopian ghost students in California that are simply AI agents attending remote classes and defrauding the financial aid system. Such invalid traffic isn’t just about advertising fraud—it’s intricately tied to privacy and security.
Bots capable of sophisticated data harvesting operations exacerbate privacy risks exponentially. These automated actors not only compromise individual privacy by gathering PII but also pose direct risks to business continuity through malicious payloads and crippling fines. How companies manage human vs. non-human traffic and protect data from automated threats significantly impacts operational security.
Data Privacy + Data Security: A Single Holistic Practice
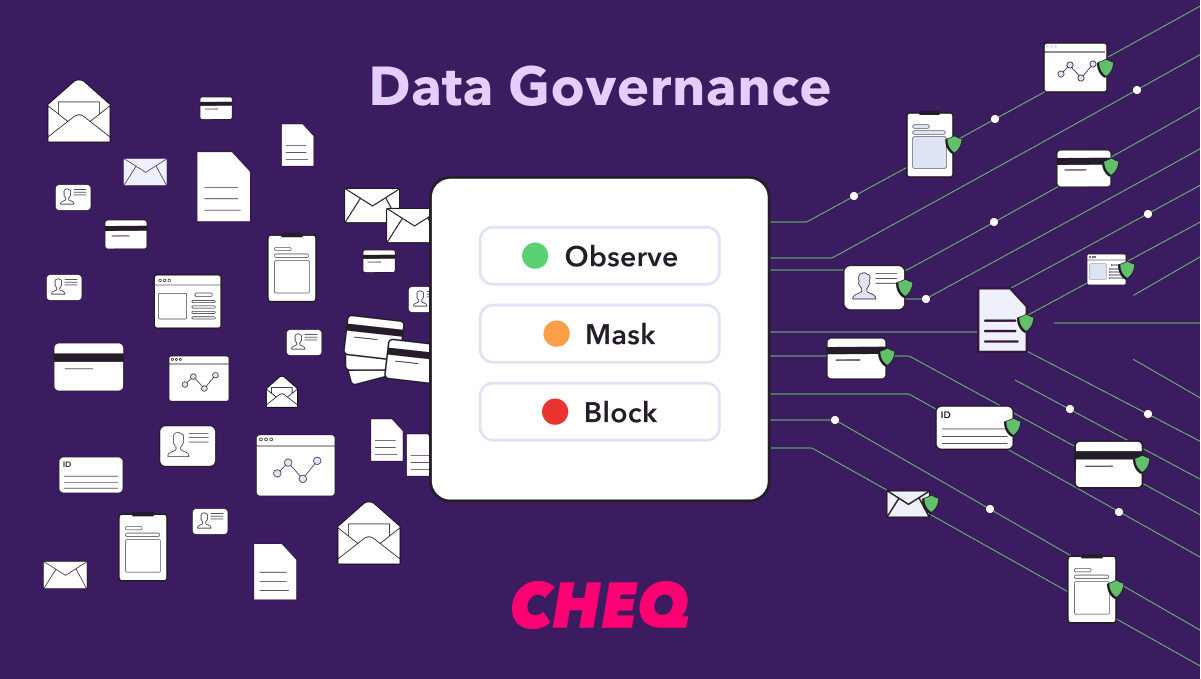
The separation between data privacy and data security has become artificial and dangerously obsolete. Effective protection demands a unified strategy, merging data privacy practices—focused on user consent and respectful data use—with robust security controls aimed at protecting data from misuse, theft, or inadvertent exposure.
Organizations need comprehensive solutions capable of understanding and mitigating threats beyond cookie tracking. This means integrating privacy-by-design principles directly into technological infrastructure, adopting proactive bot detection and AI-driven security analytics, and continuously auditing not just user-facing toggles, but every stage of data flow and partner interaction.
Trust but Verify
If Google—a tech giant with nearly limitless resources—failed users by ignoring their explicit privacy choices, can we genuinely believe smaller entities without similar scrutiny do better? The lesson is clear: robust privacy and security require vigilant oversight, transparency, and accountability far beyond the trust placed in settings and toggles alone. This does not just apply to marketing vendors, but also to partners and internal teams. Without robust and automatically enforceable security controls, anyone can put your company at risk. A rogue marketer is just as likely as a rogue vendor.
As we begin this journey with “the CHEQ Up,” we aim to peel back the layers, expose hidden vulnerabilities, and champion the urgent necessity of merging privacy and security into a single, powerful practice. Together, let’s move beyond misguided obsessions and superficial controls toward a deeper, more trustworthy digital future.
The CHEQ Up Podcast | Episode 1 | Google’s Texas Run-In ft. Jason Patel
In this episode, we unpack the Google Texas incident with Jason Patel, Field CTO at CHEQ. We explore what happened, the regulatory fallout, and why it matters for organizations everywhere.
Jason brings years of experience in privacy and compliance, having previously served as CTO at Ensighten and now part of CHEQ’s leadership team. He shares sharp insights on how enforcement actions like this shape best practices—and what teams should watch next.