Top Cyber Security Threats Affecting Go-to-Market Strategies
Yoel Israel
|Cyber Risks & Threats | February 07, 2023

About the author:
This post was written by Yoel Israel, the CEO of Wadi, the leading digital agency that specializes in digital marketing for cybersecurity brands, and Cyfluencer, a content-sharing platform for cybersecurity vendors & influencers.
Cybercriminals are an increasing concern for companies worldwide. Cyber-attacks have become a popular way for criminals to extort money, steal company data and secrets, disrupt operations, and tarnish brand reputation. While many companies prioritize revenue-generating investments during harsh economic times, modern cybersecurity systems are necessary to protect revenue, trade secrets, and brand image.
Companies can be most vulnerable to cyberattacks during a Go-to-Market (GTM) strategy. Since GTM strategies are costly, time-consuming, and vital to achieving revenue goals, any disruption to a GTM strategy can be devastating. By understanding the top cyber security threats that affect GTM strategies, you can build up your company’s defenses and protect your investments.
What is a Go-to-Market Strategy?
A Go-to-Market strategy (GTM) is an action plan that outlines how a brand will reach target customers, launch new products or services, implement new strategies or systems, or achieve other business goals.
Companies use GTM strategies to create comprehensive timelines that communicate to stakeholders the step-by-step process, desired outcomes, and how to measure success.
There are numerous benefits to creating GTM strategies:
- Reduces time to market for products and services.
- Outlines plan and responsibilities for internal and external stakeholders
- Improves probability of success
- Mitigates risk for additional costs
- Implements scalable solutions for business growth
- Allows for strategy adaptions
- Ensures positive customer experience
With GTM strategies, brands can create organized systems and structures that reduce operational costs and increase the probability of success.
The Top Cyber Threats Facing GTM Organizations
GTM strategies provide companies with a valuable framework to bring new products, services, systems, and structures to life. While GTM strategies already have inherent risk factors, cyber threats can cause detrimental harm to businesses.
To avoid cybercrimes, companies should understand the various threats they face and how to avoid them.
1. Bots
Bots are a popular tool for many web developers to improve customer experiences. However, cybercriminals can easily create malicious bots to harm your operations.
Cybercriminals will create a network of bots to overwhelm security systems and disrupt digital operations such as websites, servers, payment systems, etc.
GTM strategies are at risk from bot attacks because they generally rely on precision timing and increased operational capacity.
For instance, a business launching a new product may expect 10x the regular web traffic. Bot attacks can cause websites to shut down, payment systems to malfunction, and other technical difficulties. This can diminish the effectiveness of a product launch, negatively impacting ROI and business growth.
To stay prepared, companies should understand the different types of Bot attacks:
Form Bots
Form-filling bots are typically programmed to use stolen customer data to fill out forms and defraud, disrupt, or manipulate companies by providing useless or misleading data.
Account Takeovers
Account takeovers will use bots to access a company’s bank info, payment info, or other information to gain unauthorized access or create fraudulent transactions.
DDoS Attacks
Distributed denial-of-service (DDoS) attacks use bots to overwhelm websites, servers, and digital systems with fake traffic to shut down servers and cybersecurity systems to gain access to valuable information.
2. Ad Fraud
Ad fraud is another style of attack companies may encounter where cybercriminals use bots and malicious software to gain information, mislead companies, or disrupt operations.
Cybercriminals can use ad fraud tactics to scam companies out of marketing spending and limit operational functionality. These tactics can negatively impact any GTM strategy by wasting company time, money, and other resources.
Companies should understand the types of ad fraud scams to stay vigilant:
Ad Injections
Cybercriminals use Ad injections to replace existing ads with their own through malicious software. These fraudulent ads can carry malicious software, disrupt company websites, or advertise without paying.
Cookie Stuffing
Cookie stuffing is a form of affiliate marketing fraud. Companies will pay out advertisers and other websites that send users to their websites. However, cybercriminals can use cookies to gain commission without the company gaining any real traffic.
Click Spam
Similar to ‘Cookie Stuffing,’ click spam is when a cybercriminal fakes clicks to receive a commission from a company.
3. Client-side Attacks
Client-side attacks are when companies download malicious content that allows hackers access to company systems and data.
Client-side attacks are initiated by users within a company that takes the bait from hackers. The best way to defend against these attacks is to educate employees to watch out for malicious links, downloads, and other harmful software that could initiate a client-side attack.
To protect your operations and GTM strategies from Client-side attacks, companies should be aware of the following tactics:
Web Skimming
Web skimming is when an attacker injects malicious code into a website to gain information from a user. This information is then sent to a server that the hacker controls.
Formjacking
Formjacking is when cybercriminals use malicious code to take over the functionality of a site’s form page to collect information like login credentials, payment info, and more.
Cross-Site Scripting (XSS)
XSS attacks are when hackers inject malicious software into a company’s website to go after customer information. Cybercriminals will target seemingly safe websites that customers where customers wouldn’t expect a hack to occur.
4. Consumer Data Risks
When companies don’t implement the right cybersecurity measures, the risks go beyond lost data and disruptions to GTM strategies.
Customers who suffer from a data leak or scam by using your website will lose trust in your company. Further, by allowing cybercrimes to affect your customers, you can open your business to certain fines and litigation.
Companies should be aware of these risks when creating a GTM strategy:
Brand Reputation
Customers who become victims of fraud and data leaks are less likely to trust that company. The effects on brand reputation can last years and weaken any upcoming GTM strategy.
GDPR Fines
Many governments, like the UK, impose fines on companies for allowing data leaks and cyberattacks to take place. Failing to protect your customers can cost your company up to 4% of its annual revenue or more.
How to Protect Your Revenue with Go-to-Market Security
Investing in cybersecurity systems is the best way to protect your GTM strategy.
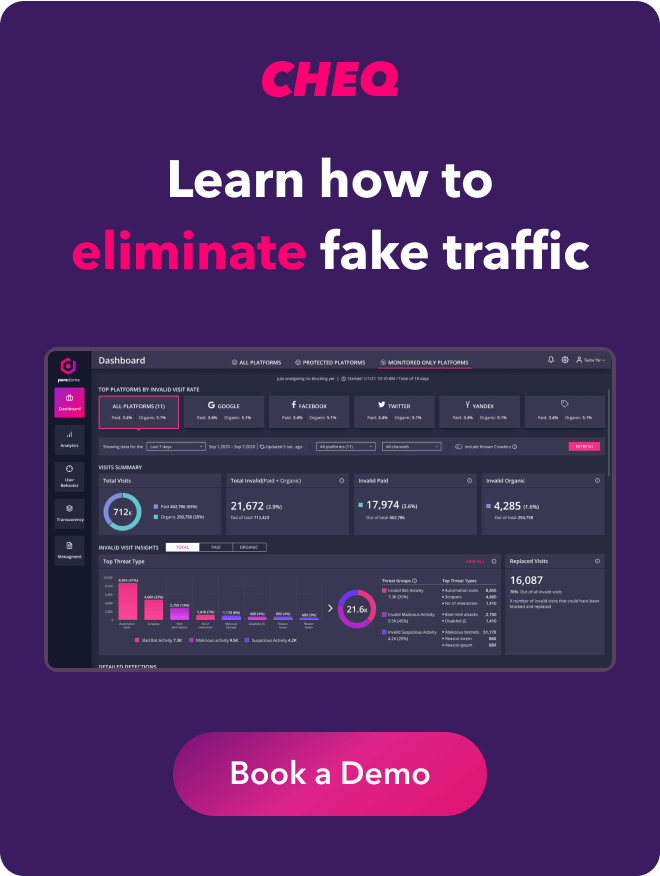
Software like CHEQ provides companies with tools and strategies to help reduce risks and let companies focus on their GTM strategy. CHEQ’s GTM security software secures data, scans for bots, ensures user authenticity, and blocks suspicious browsing patterns.
Securing Your Bottom Line
Cybersecurity has never been more critical as companies rely on e-commerce sales and digital capabilities to engage customers and grow their brands. By investing in cybersecurity systems, companies can reduce their exposure to cybercrimes and protect their customers and profit margins.
Companies should take special care in their cybersecurity when launching a GTM strategy. During these times, companies are the most vulnerable to attacks. Using tools like CHEQ’s GTM security software, organizations can ensure the success of any GTM strategy.