6 Ways CAS Unlocks Business Opportunities
Kerry Coppinger
|Marketing | September 08, 2021

Customer Acquisition Security, commonly known as CAS, is a strategy for using cybersecurity techniques to protect all the assets that help a business grow and thrive. CAS is a way of mitigating invalid traffic and digital threats, while consequently improving operational efficiencies and productivity. As you may have heard, CAS is being adopted globally by smart CMOs and other business leaders, and cybersecurity technology is being added to the tech stacks of various departments rather than just sitting with information security professionals. You may already be curious about CAS, and you may even know a few of the benefits or applications. CAS is very expansive and has a variety of use cases. Throughout this article, we’ll cover 6 of the main ways Customer Acquisition Security unlocks business opportunities and how you can apply these concepts to your own organization.
1 – Revenue
Valuable time, resources, and budget go into attracting new potential customers. By protecting all of your digital platforms with cybersecurity technology, you can not only reduce the number of invalid users that interact with your campaigns, but also replace those invalid users with real genuine users who have potential to convert into paying customers. By increasing the number of valid users engaging with your campaigns, you therefore increase the number of users who can contribute to pipeline, and revenue as well. You are able to reduce the amount of budget wasted on bots and fake users and make every dollar count. This way, you are filling your funnel with more potential customers and fewer potential threats.
2 – Audiences
When you target users based on demographics, location, or any other key identifier, they are typically grouped into audiences that can then experience your campaigns and digital content online. By utilizing CAS technology to ensure these audiences are free from invalid users, you can prevent your campaigns from skewing toward anyone who is unlikely to convert or become legitimate customers. This can be especially important for remarketing campaigns. By using cybersecurity to mitigate risks, you avoid remarketing to the same fake users over and over. Each audience can be more effective and only show your ads to those in your ideal customer profile.
3 – Optimization
Campaigns should be optimized toward users who are most likely to become customers. Most platforms do this automatically by identifying what type of users are most engaged. They seek to optimize toward whoever is contributing the most clicks, shares, visits, and interactions. That’s why it’s so important to eliminate any invalid users from all campaigns. By utilizing CAS technology, you can ensure campaigns are optimized toward real users who are actively interested rather than invalid users who are posing as potential customers. This way, you can continue to get your assets in front of more and more potential customers over time rather than diminishing the value of your campaigns by unknowingly optimizing toward fake users and bots.
4 – Conversion Funnels
While invalid users cannot become legitimate customers, they do sometimes fill out forms, request demos, or otherwise engage with your website in a way that might incorrectly identify them as a lead. When CAS technology is implemented, it significantly reduces this problem. By blocking invalid users from entering your funnel, you are able to better allocate resources and time toward real legitimate leads. Business development teams can spend their time more effectively reaching out to individuals who have a real possibility of becoming customers, rather than changing workflows and drip campaigns over and over when the real reason they’re not yielding results is because they are targeting bots and fake users. Cybersecurity can provide more accurate insights into conversion tactics in this case and overall increase productivity.
5 – Analysis
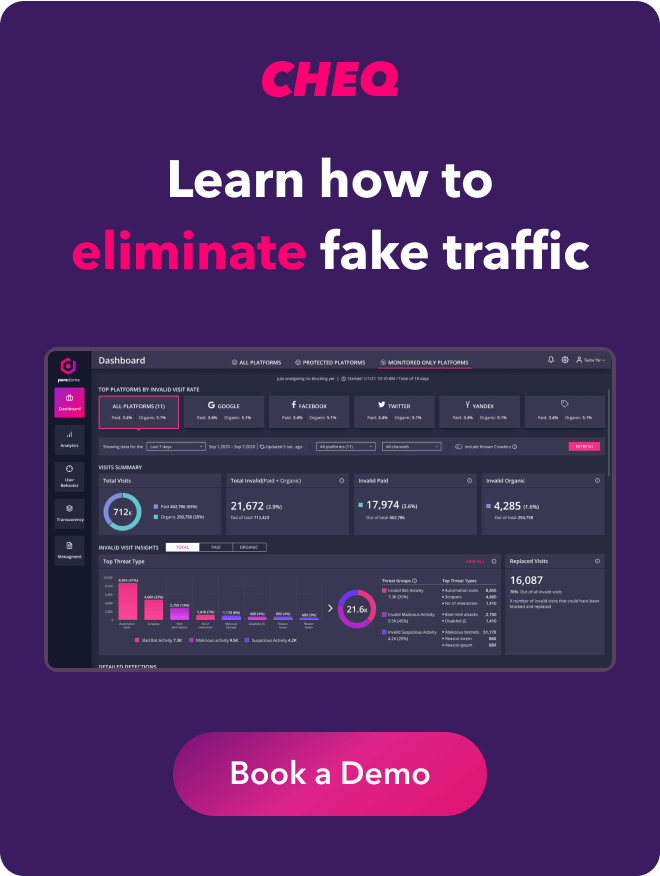
Many CAS technology providers offer independent analysis of both your current invalid traffic levels, as well as where that traffic is coming from, and what potential results you could see if those users were blocked. This provides an independent look at how your assets are currently performing and where they could improve. Since nearly every website experiences some level of invalid traffic, understanding the threats your particular business is dealing with from an objective perspective can be incredibly useful. These tools allow you to export very detailed log-level reports and generate actionable insights moving forward.
6 – Data & Analytics
Virtually all important business decisions are made based on some form of data. So it goes without saying that data should be accurate and free from major errors. However, even some of the most advanced analytics platforms fall short when identifying invalid users. That is another important area where cybersecurity can be useful. By filtering out invalid malicious users, suspicious users, and bots from your analytics tools, you can get a more accurate picture of who is interacting with your website, where they are coming from, and what type of behaviors they are taking. Spending hours making changes to better suit fake users simply doesn’t make business sense, and organizations that care about accuracy should plan accordingly.
Overall, there are several reasons a business might benefit from implementing CAS strategies and technology. CHEQ is the premier leader in Customer Acquisition Security and democratizing cybersecurity for CMOs and executive leadership. Whether you are a CMO, or a team member who is looking to improve the way your company operates, it’s a good idea to research and potentially implement threat mitigation measures.
Want to protect your sites and ads? Click here to Request a Demo.