The Ultimate Guide to Go-to-Market Security (GTMSec)
Kerry Coppinger
|Data & Analytics | July 07, 2021

Go-to-market organizations often prioritize bringing in new customers or convincing people to buy their products or services. Naturally, this applies to any business. However, it is important that the leads you are collecting are real users with no malicious intentions. Unfortunately, regardless of where your traffic is coming from or how perfectly you optimize your website, there is a strong chance some level of invalid activity is happening within your acquisition funnel.
In fact, data suggests that this past year, $3.8 billion was wasted on invalid activity within the eCommerce sector alone! This includes bots cycling through website landing pages, scraping contacts, committing chargeback fraud, or filling in fake reviews. These are also leads that will never become customers.
So what can you do to ensure you are spending your valuable time and budget acquiring leads that can actually convert?
It’s time to talk about Go-to-Market Security, commonly referred to as GTMSec.
GTMSec is an overarching business strategy that ensures legitimate users are interacting with any assets throughout the GTM funnel.
Protection of GTM is vital for all customer acquisition channels, including (but not limited to) advertisements, website content, CRM management systems, analytics, and reporting. This post covers everything you need to know while getting started with this strategy and also outlines key terms to know and goals to keep in mind.
Some key reasons to prioritize GTMSec include
Skewed Analytics
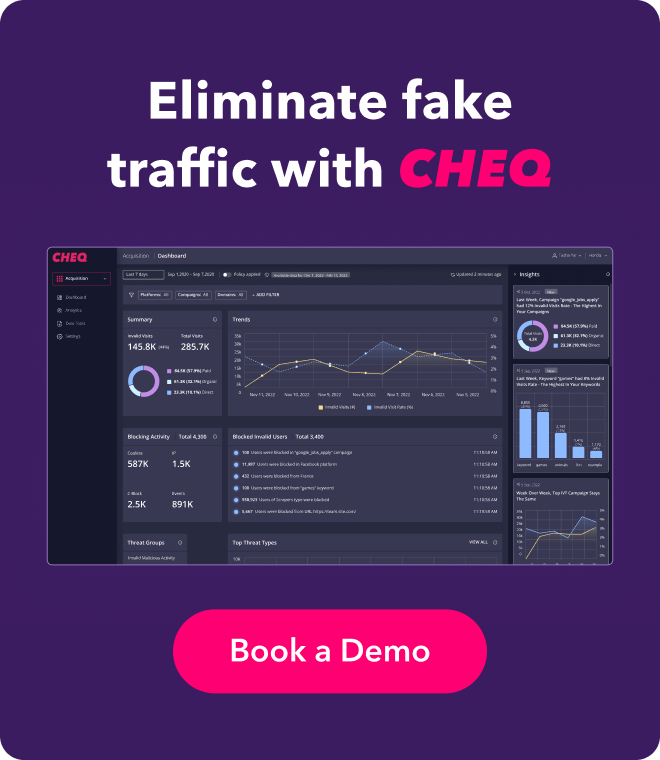
Every company refers to itself as “data-driven”. This means decisions are typically made based on some form of data and analytics. However, if your analytics don’t paint an accurate picture of what’s really happening in each of your acquisition channels, then you end up making decisions based on data that is incorrect. Due to the large quantities of bots, malicious users, and suspicious users, this issue affects a vast majority of businesses – sometimes without their knowledge. By prioritizing GTMSec, you ensure the analytics you’re looking at are highlighting the activity of valid users. This way, you can make smarter business decisions and create a more predictable decision-making process.
Polluted Audiences
When targeting a specific audience, or ideal customer profile, you’ll want to make sure the members of that audience are valid users rather than bots or other forms of invalid users. Because invalid users exist all over the internet, it is highly likely that they could accidentally become part of your target audience even though they have no potential to turn into real customer. GTMSec can help you avoid this “pollution” and replace inaccurate and invalid audiences with protected audiences. By prioritizing this at the start of the funnel, it also increases the chances of cleaner audiences throughout the customer journey.
Skewed Optimization
When a certain type of user clicks on one of your assets – typically either an organic link or a paid advertisement – the internet then optimizes your asset toward that type of user. This is known as asset tracking, and it’s a great way to make sure that your website is always catering to the right audience. But what happens when invalid users or bots are frequently clicking on these assets? As you can imagine, clicks are then optimized toward that type of user which could create a snowball effect of more and more invalid activity. To stop this in its tracks, GTMSec technology can unskew this optimization and redirect your efforts toward more valid users. This can be incredibly helpful in maximizing the impact of a campaign.
Resource Misuse
When your assets are not performing as predicted, teams can pour a lot of time, effort, and money into getting to the bottom of what’s not working. But if the real reason assets are not performing as expected is that invalid users are causing inaccuracies, then all those valuable resources might have been misused. Imagine setting up A/B tests, trying out new creative, changing keyword strategies, trying out new platforms, when all along performance was just being affected by invalid users. This happens all too often, and GTMSec can help.
Missed Revenue Opportunities
When your channels are not protected, and invalid users enter your funnel, they are taking the place of valid users who could potentially turn into paying customers. So not only are invalid users causing an inconvenience by cluttering your website and funnel, but they are also reducing the amount of revenue uplift you could be seeing if you were to replace them with additional customers. GTMSec has the potential to unlock more revenue for your business with minimal effort from your team. Before you start looking for new ways to increase profits, consider unlocking the potential paying customers that could be signed if the existing budget was moved away from fake users and to real buyers and advocates of your product or service.
The three major types of threats your funnel can encounter are:
Malicious Users
Malicious users commit excessive, non-standard activities or false identity actions with malicious intent. These types of activities have a harmful impact on your digital efforts. They are detected by analyzing the user’s behavior and characteristics. In order to optimize your customer acquisition funnel, these users should typically be blocked or removed, as they do not serve any helpful purpose. By contrast, they skew data and cause major operational mishaps.
Suspicious Users
Suspicious users are typically users who repeat an activity an abnormal amount of times, or users who come from a suspicious source. Many suspicious users arrive through VPNs or proxies. While suspicious users do not necessarily have poor intentions, they should be monitored as their ultimate goal and viability is not clear. However, these types of users should be analyzed separately from malicious users for a clearer picture of what is causing issues within your funnel.
Bots
Unlike suspicious and malicious users, bots are not real users at all. They are automated software programs that can perform a variety of actions. Bots typically imitate or replace human user behavior. These non-human tools can be used for malicious purposes, such as false clicks or other types of fraud. However, they can also be used for non-malicious purposes such as indexing content. Either way, they are not real users and cannot turn into real paying customers.
When implementing GTMSec technology, there are two main phases that serve to clean up your funnel and bring more customers
Monitoring
Before you dive head-first into blocking all invalid traffic, it’s important to first evaluate what is happening on each of your channels. The channels you’re assessing during this time are known as monitored platforms. Different types of fake users or invalid traffic affect channels differently, from Google to Facebook, to LinkedIn, Pinterest, and Instagram. This monitoring phase can allow you to identify the biggest threats to your specific customer acquisition funnel and then plan your strategy accordingly. This is especially important if you are new to GTMSec tactics or if you are experiencing a lot of invalid traffic and want to identify where it’s coming from.
Protected
Once you’ve monitored each of your platforms, it’s time to make some decisions in order to secure your customer acquisition funnel. When you decide to protect a given channel against invalid users, it is then considered to be in the protecting phase and is ultimately labeled as a “protected” channel. The more channels you protect, the more accurate your data is, and the more opportunities you have to convert real valid users.
Some metrics you might consider measuring are:
Invalid Rate (IVR)
IVR is the rate, or percentage, of activity within your funnel that is invalid. Not all invalid clicks are necessarily malicious, but regardless of intention, it is helpful to identify how much of the activity on your website will never turn into a real paying customer. It is important to keep in mind that new invalid traffic enters the online ecosystem continuously, and it is nearly impossible to have an invalid rate of zero. However, by monitoring this metric, we can work towards getting that number under control while minimizing the chances of the same invalid user causing clutter in your funnel over and over again.
Average Repetitions
This is the number of times a single invalid source is expected to revisit your site or submit some sort of action or activity if it is not controlled or blocked. For example, if you do not block a competitor from clicking on your ads, average repetitions will tell you how many times they would continue to click. Similarly, if you do not filter out scrapers from your analytics, average repetitions will tell you how many times they would continue to pollute your traffic. Understanding the threat of repeated activity can help you prioritize channels that have a high number of average repetitions.
Benefit Range
Benefit range is a scale of how much improvement your business might see when GTMSec technology is implemented. This metric includes both a minimum and maximum number to give you a full picture of the results you can expect. It is most accurate to present a range in this case rather than just one number, because overall benefits depend on a variety of factors. GTMSec measures can ensure more real users are entering your funnel.
Replaced Visits
This is the number of visits gained from valid users once GTMSec tactics are implemented. They are called replaced visits because they substitute the invalid visits you were previously receiving with real potential prospects. Before protecting your platforms, you can predict the amount of potential replaced visits. Then, when you protect your accounts and watch the results come in, you can see the actual calculated number of visits that are replaced. It is important to pay attention to both of these numbers.
Taking for instance one sector (online gambling) we see how this works. The online gambling industry’s digital spend annually amounts to £747m on direct online marketing, £301m through “affiliate” websites such as tipsters. Overall, at present $1.7 billion is spent online by those running gambling sites and apps, acquiring 5.8 million customers a year. The sector has a roughly 3x CAC to LTV ratio, bringing an average of $1129 per customer in average lifetime value. With 17% invalid bot and fake user clicks in the funnel the effects on potential growth are stark. If bots were eliminated from customer acquisition channels, online gambling would win an additional 791,000 more customers. This amounts to a revenue uplift of $893 million. This is a nice win.
Overall, GTMSec is moving from an innovative concept that helps companies optimize campaigns, to an essential strategy. Understanding and adopting a GTMSec approach is crucial for CMOs, VPs of marketing, demand gen leaders, and revenue operation professionals to ensure the highest levels of efficiency and ensure companies are following the real data. Whether your personal emphasis is on marketing, analytics, lead nurturing, new business outreach, or another aspect of customer acquisition, GTMSec can help your department work smarter. To learn more about GTMSec, and how you can easily apply it to your business through cyber security technology, contact our team of experts today and request a demo.