Cryptojacking: What is it And What You Need to Know in 2023
Jeffrey Edwards
|Cyber Risks & Threats | May 11, 2023

It’s a bit like someone else borrowing your car to drive deliveries and earn money behind your back, using up your gas and leaving you with added wear and tear on your vehicle in the process.
Breaking Down a JavaScript Crytomining Attack
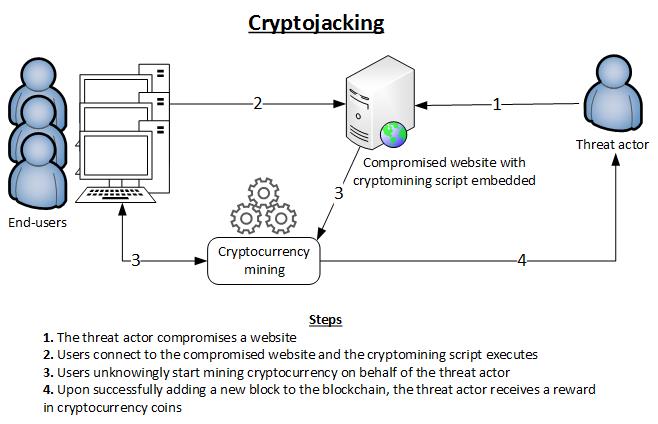
The image above succinctly describes the process of a client-side cryptojacking attack, but to better understand this process, let’s take a closer look at the steps in the attack. For a more detailed breakdown of common cybersecurity attack techniques (and how to mitigate them), check out our recent blogs on Cyberattacks and the OSI model.
Step One: Finding an Injection Point
For starters, would-be attackers need to identify a target. To do this, hackers may employ automated scanning tools, such as vulnerability scanners or web application scanners, to quickly scan a large number of websites for common security issues like outdated software versions, misconfigurations, or known vulnerabilities in web applications. They may also target specific web application frameworks or popular plugins in a supply chain attack.
Step Two: Creating Malicious Code
Once a target has been selected, the attacker crafts a piece of JavaScript code specifically designed for cryptocurrency mining. This may sound complex, but the barrier to entry is actually shockingly low.
Simply signing up for a mining pool and pasting a couple of lines of code into the source of a website is all it takes for an attacker to set up a shop.
Cryptojacker’s code typically uses libraries or frameworks which provide out-of-the-box mining functionality. These tools provide a pre-written JavaScript code snippet that typically contains the necessary mining algorithms, communication protocols with mining pools, and configurations for mining parameters.
And hackers aren’t limited when choosing how they are going to inject a miner into your website. In the course of our research, we found thousands of live samples, including cryptoloot, coinimp, jsecoin, crypto-webminer, cryptonoter, monerominer, deepminer, and coin-have.
The code used by the mining operations is top-notch. It’s designed using the latest technology to get the most out of a computer CPU. Hackers implement web assembly, a portable binary code in javascript capable of utilizing low-level languages such as C, so miners are able to get the most from the CPU of website users. This not only gives them the best access to the victim’s CPU for computation but has the added benefit of being really hard to detect by reading the source code of a website. In the industry, we refer to this technique as obfuscation.
Step Three: Code Injection
Next, the attacker injects the malicious JavaScript code into the target website or web application. There are various methods for injection, including exploiting vulnerabilities like Cross-Site Scripting (XSS) or directly modifying the website’s source code.
Step Four: Execution and Mining
Now, when a user visits the compromised website, their browser loads the web page and executes the injected JavaScript code automatically. The code runs in the background, leveraging the user’s device’s processing power. The mining script collaborates with other miners in a mining pool or operates independently.
It continuously solves cryptographic puzzles or algorithms to validate and confirm transactions on the cryptocurrency network. Once a miner successfully solves a puzzle, they create a new block and receive a reward in the form of cryptocurrency.
As the mining process progresses, the victim’s device experiences increased CPU or GPU usage, causing the system to work harder and generate additional heat. This can lead to device slowdowns, reduced battery life, and potential hardware damage in extreme cases.
While researching Cryptojacking, our laptops heated up, and fans kicked on. Cryptojacking not only degrades the performance of users’ computers but shortens the life of their computer’s components. For site owners, cryptojacking degrades page performance as well as user experience, ultimately driving visitors away from your site.
Step Five: Concealment and Persistence
To avoid detection, the attacker may use techniques like code obfuscation or periodically change the location of the injected script.
How prolific is cryptojacking?
In our research, we saw compromised websites as low as personal blogs up to top Alexa-ranked websites being affected by Cryptojacking. No single vulnerability is being exploited to compromise these websites but we are seeing an uptick in mining operations online.
Historically, cryptojackers either leveraged JavaScript-based cryptojacking services, such as Coinhive, which gained attention in 2017, or relied on compromised plugins or malicious browser extensions to deliver malicious JavaScript.
One notable example is the faceXworm attack, which used social engineering techniques to trick users into downloading and installing a malicious browser extension, which gained access to the victim’s Facebook account and sent malicious messages to the victim’s friends, further spreading the infection.
The extension injected malicious JavaScript code into Facebook pages, enabling it to hijack the victim’s browsing sessions. It targeted cryptocurrency-related pages, such as those providing information about ICOs (Initial Coin Offerings), and injected cryptojacking scripts to mine Monero cryptocurrency using the victim’s device resources.
Following the cryptocurrency crash of November 2022 and subsequent lowered cryptocurrency values, some attackers have turned to new techniques that target valuable cloud and server resources for cryptomining. Some attackers have begun exploiting free trials on some of the largest continuous integration and deployment (CI/CD) services to deploy code and create distributed mining platforms, while others are targeting misconfigured Kubernetes and Docker instances to gain access to the host systems and run cryptomining software.
Other attackers have turned to targeting server-side resources. ProxyShellMiner, for example, exploits three vulnerabilities in Microsoft Exchange servers to install a Monero miner on compromised machines.
What can you do to prevent cryptojacking?
So, what can you do about cryptojacking? The first step is to know the signs. Then, as you may guess, there are two different ways of mitigating its effects: detection and defense. Detecting cryptojacking isn’t always easy, but defense is even trickier.
Cryptojacking Detection
The first thing to consider is whether or not your website is being cryptojacked. Here are some things to check:
- Are you getting HTTP requests for Bitcoin and Monero transactions on your site?
- Are you getting suspicious JavaScript errors when accessing your site?
- Does your computer heat up and run the fan when you access your website?
If you’re concerned about cryptojacking on your business network, you could also use a network monitoring tool to look for unusual resource usage.
No matter how it’s done, mining cryptocurrency is a massive resource hog, which gives some telltale signs, such as abnormally high CPU or GPU usage. Especially in off-business hours when machines should be less active. A simple way to look for abnormal use would be to set up alerts for when CPU usage exceeds a certain threshold in off-hours or on machines that don’t typically perform CPU-intensive tasks.
Defense
From the user’s perspective, the most obvious defense against cryptojacking would be to block javascript from running on their browser, but this could make for a pretty poor internet experience. However, there are plenty of browser plugins, such as No Coin and MinerBlock, that can help the user block known cryptojacking scripts.
For a site owner, things are a bit more difficult. In order to definitively prevent cryptojacking on your website, you need full visibility into the code running on your website, as well as any third-party connectors and plugins, and the ability to unilaterally block unwanted code.
A client-side security platform will let you perform frequent audits of your website’s javascript content and security and will help you block unknown scripts from ever running on the client-side, thus blocking injection-based attacks like formjacking, payment card skimming, and, yes, cryptojacking.













