Bot Mitigation: What It Is and How It Can Protect Your Site Without Hurting Your Business
CHEQ
|Cyber Risks & Threats | September 17, 2025
- What bot mitigation involves and how it typically works
- How to protect your site without hurting your business
- The problems bots can pose and how bot mitigation makes a difference
- How bot mitigation can benefit businesses in different sectors
- The most common bot attacks
- What to look for in a bot mitigation vendor
Bots have long been part of our online lives, ranging from crawlers that enhance search engine results to spambots that spread malware and phishing. How can you separate the good from the bad – and work out which is which?
That’s where bot mitigation comes in. Bot mitigation solutions identify and analyze bot interactions on your site, alert you to suspicious behavior, and enforce protections in real time. And it’s never been more important: our report on “The State of Fake Traffic 2024” found that 17.9% of all traffic monitored in 2023 was fake, compared with 11.3% in 2022. That’s a 58% increase.
A strong bot mitigation strategy helps organizations benefit from legitimate automation while preventing malicious activity. But with a range of tools on the market, what should you prioritize?
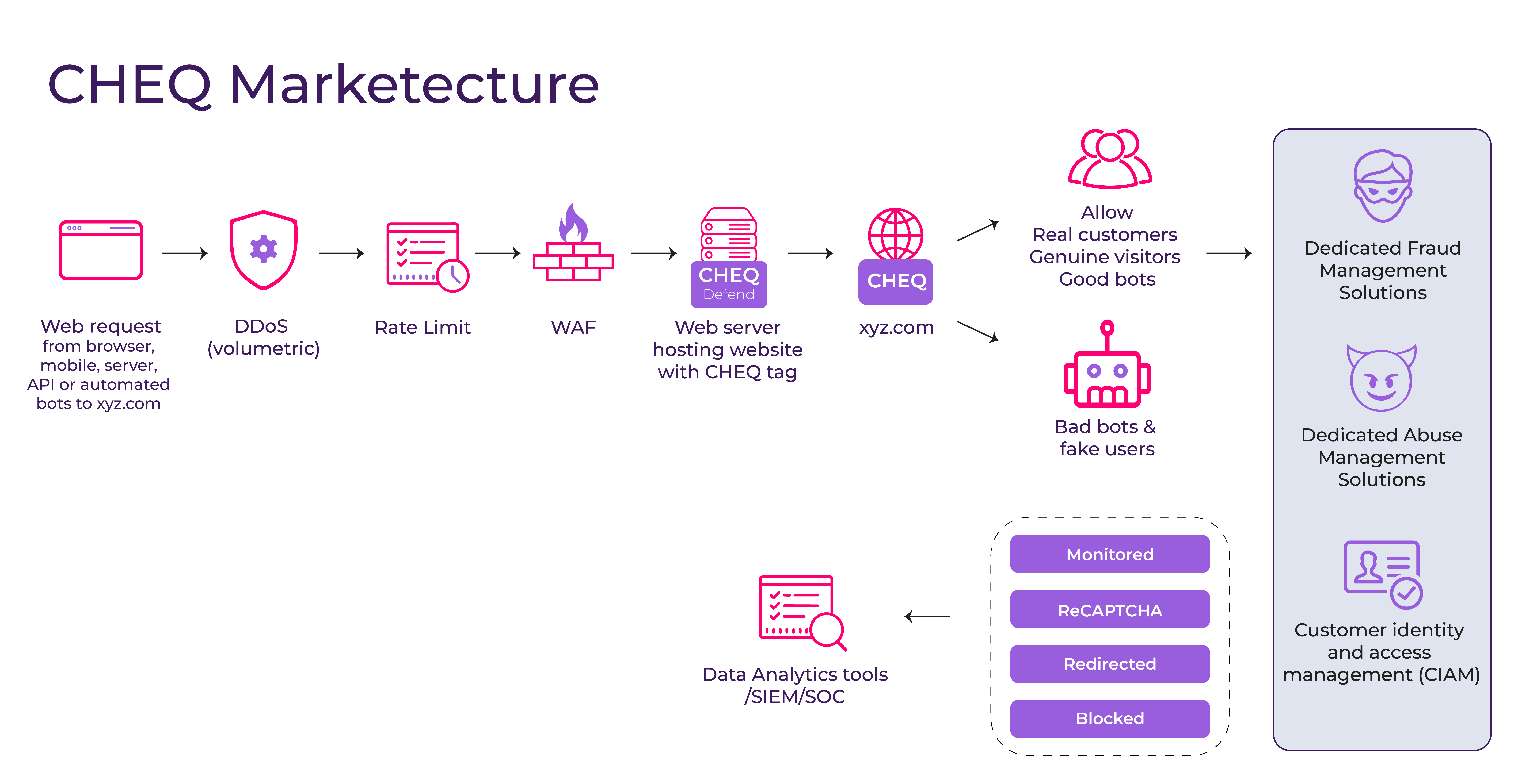
The Bot Mitigation Process
Bot mitigation identifies and blocks harmful bot traffic when it attempts to interact with a website or mobile app. The idea is to intercept malicious bots, label them as a threat, and direct them away, preventing future harm without disrupting legitimate human users or beneficial automated agents.
While the precise approach can vary, an effective solution should be built on a three-stage pipeline: detection → risk assessment → enforcement:
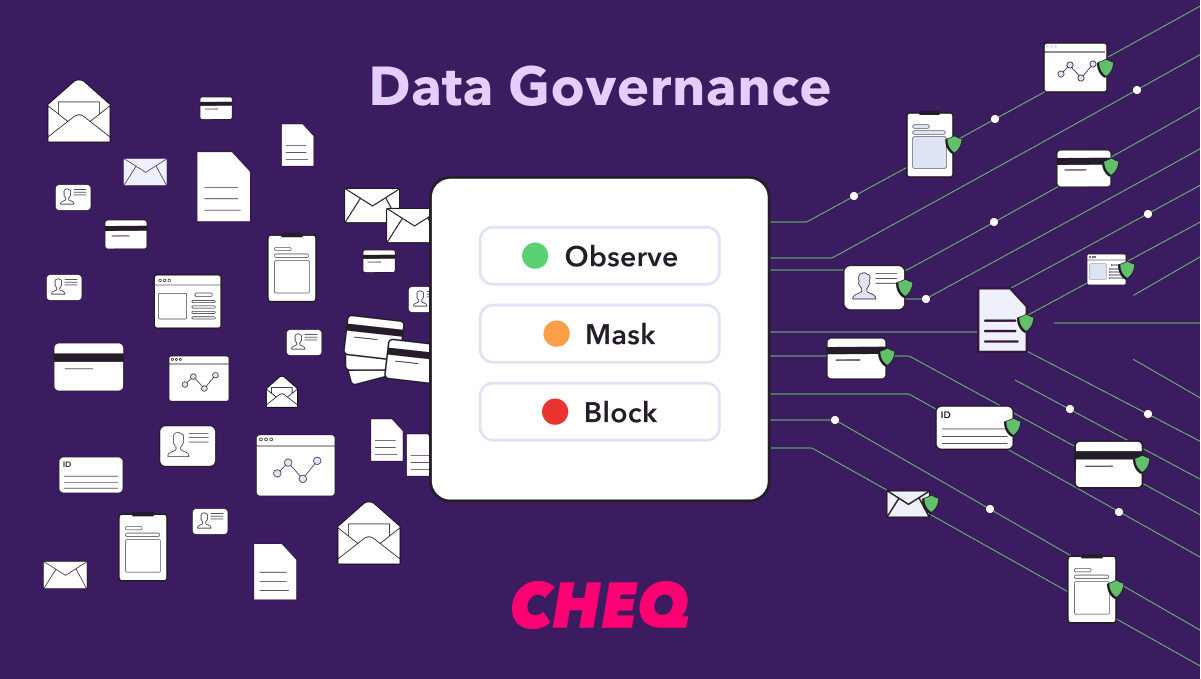
- Detection: It’s vital to first detect bot activity. At CHEQ, we focus on traffic integrity analysis, user input validation, and identity intelligence to detect different forms of bot traffic across web and mobile environments.
- Risk Assessment: Evaluate the risk and potential impact of an interaction once suspicious or malicious automation has been identified, helping determine the appropriate enforcement response.
- Enforcement: When a bot is detected, your mitigation solution needs to provide an array of tools to address any potential problem, ranging from rate limits and progressive challenges to a hard block.
Below is a simplified view of the detection → risk assessment → enforcement pipeline that underpins modern bot mitigation.
Of course, it’s important to recognize that not all bots are “bad”. Bots might represent legitimate automation, such as genuine buyers who are interested in your goods and services. Or they could be crawlers that help search engines identify and rank webpages, ultimately boosting your business’s visibility.
“You should always block harmful bots,” notes Amy Holtzman, Chief Marketing Officer at CHEQ. “But distinguishing ‘harmful’ isn’t always clear.”
This demands a comprehensive solution that begins with detection, leveraging sophisticated signals to detect suspicious bots. Risk assessment is then applied to determine the appropriate enforcement response. Finally, the process moves into enforcement and remediation, blocking malicious bots from your systems while maintaining accessibility for legitimate users and beneficial automation.
So how does this work in practice? First, let’s look at the problems that bots can cause.
What Problems Does Bot Mitigation Solve?
Bot mitigation solves the issues bots and fake users cause when they arrive on a website or a platform. Below are common on-site problems caused by malicious automation, along with their associated business impacts:
- Account takeover fraud: This is a type of cybercrime where criminals seize control of business or individual accounts online. Malicious bots can be used to execute these attacks, including through credential stuffing, where bots exploit stolen or compromised credentials in an attempt to log in to a site. Business impact: fraud losses, account lockouts, regulatory exposure, and customer support burden.
- Carding: Criminals use stolen credit or gift card details on payment portals. Bots automatically input card details to test which ones work – often leading to fraudulent purchases, inventory issues, and more. Business impact: chargebacks, payment processor risk warnings, inventory distortion, and financial loss.
- Scraping: These bots automatically harvest specific pieces of data or information; attackers use them to extract pricing, content, product listings, or proprietary data, potentially stealing your IP. Business impact: IP theft, competitive exposure, market undercutting.
- Inventory hoarding: Bots are used to add huge amounts of a certain product to online shopping carts, leading to artificial shortages, checkout abuse, availability issues, and customer frustration. Business impact: lost revenue, false scarcity, and damage to brand trust.
- Skewed analytics: You want your marketing analytics to tell you about real customers — such as signaling genuine interest in a particular product or service. However, this data could be skewed by malicious bots, potentially harming your optimization and reporting accuracy going forward. Business impact: wasted ad spend, distorted attribution, and misinformed business decisions.
- Distributed denial-of-service (DDoS) amplification: Bots are used in DDoS attacks, flooding targets with multiple messages or server requests simultaneously; this can overwhelm the target, potentially causing a website or service to slow down or crash. Business impact: outages, latency, elevated infrastructure costs, and operational disruption.
It should be noted that legacy bot mitigation does not solve threats that may occur outside an organization’s owned channels, such as advertising platforms, affiliate partnerships, or other external partners.
To address those problems, a modern, go-to-market bot management platform is required. CHEQ protects advertising and affiliate investments with its speciality solution, CHEQ Acquisition.
How Does Bot Mitigation Work?
Bot mitigation relies on a full detection pipeline, based on several crucial elements.
This includes telemetry collection to provide the data needed to separate malicious bots from human interaction and from “good” bot traffic. Feature extraction then transforms raw telemetry into meaningful attributes—such as timing signals, header values, environmental fingerprints, and behavioral patterns—that help distinguish humans from bots.
The process then moves on to sophisticated approaches that help identify malicious bots. For instance, device fingerprinting can be used to authenticate users, helping to determine if there has been an attempt at unauthorized access. IP or proxy correlation can be used to detect sophisticated or coordinated attacks.
It is then possible to determine the risk level, used to assess the potential impact of allowing the interaction to proceed and to guide enforcement actions. The process finally moves onto enforcement – blocking the bots from your site through the source IP, applying challenges, redirecting suspicious traffic, rate limiting, or issuing hard blocks for high-risk behavior.
Importantly, an effective bot mitigation system will use the data gathered to continuously improve the service through a continuous feedback loop that retrains models, tunes thresholds, and adapts to emerging bot patterns.
At CHEQ, our approach is built on analyzing weaknesses and protecting key signal families. Some of these include:
- Client Techniques: Analysis of attributes from the client machine that can be accessed via JavaScript function invocation. This could include explicit attributes, like traces of automatic browsers or malware, or implicit attributes revealing automated webdrivers.
- HTTP Techniques: The observation of abnormal headers, such as known malicious IPs.
- TCP Techniques: Fingerprinting technique that detects User Agent (UA) spoofing, which can be used for device obfuscation and to hide a device’s true location.
- DNS/STUN Techniques: Used to detect the real IP address of command and control (C&C) centers that route bot traffic through proxies or reveal inconsistencies in DNS resolution behavior.
- Network Behavioral Analysis: Used to detect coordinated attacks based on time series anomalies. For example, rules might flag IP addresses that commit transactions every “X” seconds after “Y” transactions.
- User Behavioral Analysis: A class of algorithms that predict whether behavior is a real or legitimate user by using the signals such as mouse movements, click patterns, and time between actions.
- Data Models: CHEQ uses deep learning (e.g., recurrent neural networks), machine learning classifiers, and reputation-based modeling to flag, assess risk, and prevent threats at scale.
Of course, it’s vital to minimize false positives and maintain accessibility for legitimate users, including legitimate automation such as search and LLM crawlers. CHEQ deploys multi-signal correlation and risk thresholds to avoid unnecessary friction.
| Signal Type | What It Indicates | Common Enforcement Action |
|---|---|---|
| Keystroke timing | If this is unusual – much faster typing than a typical human – it could indicate bot activity | Challenge |
| Mouse trajectories | Again, unusual patterns could indicate the presence of a bot, so it may need to be investigated to determine if it is malicious | Challenge |
| DNS/STUN anomalies | These could indicate an attack; for example, attackers may hide malware within DNS traffic. | Block |
| Header anomalies | Could include known fraudulent headers or malicious IPs | Block |
| TLS fingerprint mismatches | Indicates automation frameworks or spoofed network stacks | Challenge or hard block |
| Cookie integrity issues | Suggests tampering or replayed sessions | Challenge |
| Cross-layer RTT variance | Indicates coordinated botnet activity or synthetic session timing | Rate limit or block |
What Type of Businesses Can Benefit From Bot Mitigation?
Any business that relies on digital interactions, transactions, user accounts, or real-time inventory is vulnerable to automated threats. Businesses that depend on digital engagement often see the clearest gains from effective bot mitigation because even small volumes of malicious automation can distort revenue, customer experience, and analytics.
Bot mitigation is particularly valuable for organizations with high-value user actions (such as logins, checkouts, or form submissions) or environments where automation can provide an unfair or harmful advantage.
Common business types
A wide range of businesses could benefit from bot mitigation. For example:
- E-commerce: Bot mitigation significantly benefits e-commerce stores by safeguarding them against malicious activities that lead to lost revenue, reduced conversion rates, checkout abuse, inventory hoarding, and skewed analytics.
- Financial services: Given the highly sensitive data involved and the risk of fraud and theft, these businesses are obvious targets for malicious bots executing credential stuffing, ATO, and card testing attacks.
- Advertising and marketing: One of the significant dangers of bots is their impact on advertising budgets and analytics – for example, by draining the budget for a pay-per-click campaign, also skewing top-of-funnel analytics. Bot mitigation improves traffic quality and attribution accuracy, ensuring campaigns are optimized based on real users rather than automated noise.
- Hospitality: This sector is especially vulnerable to hoarding attacks which target limited tickets or reservation slots.
Self-identification checklist
Here’s a checklist of triggers to help determine whether bot mitigation is likely necessary. If your business possesses these key factors, it might be particularly important to consider bot mitigation.
- Account login
- Account creation
- Gift cards or coupons
- Limited-inventory drops
- Price-sensitive SKUs
- Exposed APIs
- Affiliate programs
What are the Most Common Bot Attack Types?
Bot traffic isn’t necessarily a bad thing – in fact, it can often represent real potential customers, among other positive effects. However, there are significant dangers and a range of attacks that could impact your website and service. Understanding the major attack types helps teams connect threats to the right detection signals and enforcement actions.
| Attack Type | Category | Short Definition | Detection Clue | Business Impact |
|---|---|---|---|---|
| DDoS | Performance | Automated traffic meant to overwhelm servers | Large spikes in identical requests from distributed sources | Site outages, latency, resource exhaustion |
| Fake Account Creation | Fraud | Bots creating fake profiles or registrations | Repetitive form submissions with uniform behavioral patterns | Polluted CRM and contact data, downstream fraud |
| Account Takeover (ATO) | Fraud | Using stolen credentials to break into real accounts | Unusual device or IP, failed attempts then sudden success | Fraud losses, regulatory risk, reputational harm |
| Credential Stuffing / Password Spraying | Fraud | Automated login attempts using leaked or common passwords | High velocity login attempts across many accounts | Account lockouts, compromised accounts, reputational risk |
| Carding | Fraud / Payments | Bots testing stolen credit cards in large volumes | Many small transactions with high decline rates | Chargebacks, merchant account risk |
| Scraping | Abuse | Automated harvesting of data, content or pricing | Fast, sequential fetches without human interaction | IP theft, competitive exposure |
| Scalping / Inventory Hoarding | Revenue Distortion | Bots buying scarce items faster than humans | Unrealistic carting or checkout speeds | Lost sales, customer frustration |
| Click or Affiliate Fraud | Revenue Distortion | Fake clicks to inflate ad spend or commissions | Zero engagement sessions with non-human timing | Wasted budget, corrupted attribution |
| API Abuse | Abuse | Hostile or automated misuse of API endpoints | Abnormal call frequency or malformed requests | Service strain, data leakage |
These dangers are very real, but they can be addressed: with the right technology, organizations can detect, classify, and block malicious automation, while investigating those in the “grey zone” before deciding whether to admit them to your site. Recognizing these attack categories also helps security teams align each threat with the appropriate mitigation strategy.
What are the Most Common Bot Mitigation Strategies?
No single signal is absolute when it comes to detecting and mitigating malicious bots: vendors rely on multi-signal correlation across different layers to determine the nature of the threat and the required action. This correlation helps reduce false positives and improves accuracy across web and mobile environments.
At CHEQ, we divide this into three detection layers, focused on traffic integrity analysis, user input validation, and identity intelligence. Together, these layers for web and mobile help determine attacks across signals, whether it’s a headless browser, disposable/temporary emails, or impossible travel, when a person’s activity seems to occur in geographically remote locations within a short timeframe.
| Detection Layer | Strategy Examples | What It Helps Detect |
|---|---|---|
| Traffic Integrity Analysis | Automation framework detection, headless browser indicators, spoofed UA/platform, DOM tampering, location masking, fingerprint inconsistencies | Bots, scrapers, agent impersonators, fake sessions |
| User Input Validation | disposable/temporary emails, malformed fields, phone validation, text entropy patterns, domain age checks | Bulk form spam, synthetic leads, automated submissions |
| Identity Intelligence | Familiar device/IP recognition, impossible travel, new ASN/network, address or email cycling, identity graph verification | Fraudulent users, account takeover attempts, synthetic identities, and coordinated identity-based attacks |
When the evidence points to bot activity, multiple enforcement options are available, depending on risk and confidence. For example, you could protect forms by redirecting the bot to a “honeypot,” a hidden form or field that is only visible to bots, not humans: if the bot fills in the form, you know to filter out that submission (or use the data to learn more about the bot).
You could also apply rate limiting—restricting how often someone can perform a particular action in a given timeframe – or escalate to a hard block. Additional enforcement options include soft blocks, tarpitting (slowing sessions), challenge routing (CAPTCHA or JS challenges), or serving alternate content for high-risk sessions. It’s important to affirm legitimate users and legitimate AI agents to avoid unnecessary friction, ensure they are not caught in aggressive enforcement flows. Progressive enforcement (increasing friction only as risk rises) helps control false positives.
Your chosen course of action depends on the confidence of classification and the risk associated with allowing the interaction, as determined by policy and risk thresholds.
What Should Companies Look for in a Bot Mitigation Vendor?
Modern bot mitigation platforms rely on deterministic detection and high-confidence classification to identify malicious automation, combined with policy-driven enforcement to protect sensitive flows without disrupting legitimate users.
A strong bot mitigation vendor should clearly explain:
- Which signals led to a classification decision
- Why an interaction was allowed, challenged, rate-limited, or blocked
- How enforcement policies balance security, business risk, and user experience
This level of transparency is a core CHEQ differentiator.
Effective platforms provide visibility into detection coverage, enforcement outcomes, latency impact, and false-positive rates, enabling teams to validate decisions and continuously tune protections as attack patterns evolve.
In addition to accuracy, buyers should evaluate deployment flexibility (for example, WAF or CDN integrations, edge or origin deployment models, and mobile SDK support) and the vendor’s ability to handle mixed traffic environments that include human users, legitimate automation, AI agents, and malicious bots.
Buyer checklist
- Accuracy: Multi-signal correlation across device, network, and behavior.
- Coverage: Protection for web and mobile app traffic across high-risk flows.
- Latency: Minimal impact on page speed and customer experience.
- Transparency: Clear explanation of signals and enforcement decisions.
- False-positive control: Tools and thresholds to minimize friction for legitimate users.
- Deployment flexibility: Support for edge/origin deployments, WAF/CDN, and mobile SDKs.
- Traffic mix readiness: Ability to distinguish and appropriately handle human users, legitimate AI agents, and malicious bots.
- Relevant use cases: Does the vendor work with similar companies or industries to your own? Do they solve similar issues to those you face?
Final Thoughts
Bots are going nowhere, especially in the age of AI-driven traffic, so it’s important to separate the good from the bad – and carefully examine everything in between. At CHEQ, we believe it is essential to strike the right balance between explainability and granularity: users need clear insights built on the right data to show why a session was classified as malicious.
It isn’t about preventing all bots. On the contrary, it’s about illuminating the picture – working out what you want in your site, what should be prevented, and acquiring the tools to achieve your goals.
Get in touch with CHEQ today to book a demo and learn how we can help protect your business from the dangers of malicious bots while enabling it to reap the benefits of genuine human interaction and legitimate bots.