All About VPNs and Click Fraud
Oli Lynch
|Marketing | August 20, 2020

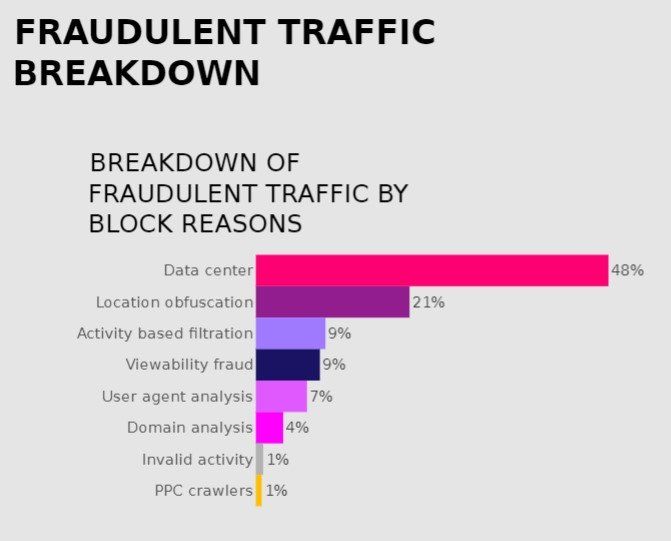
One in five click fraud cases involve VPNs or proxies
The VPN, or virtual private network, can be a useful tool for the casual internet user. These software plugins can help hide your location and make it easier to be anonymous online for a whole variety of reasons. And, of course, masking your location also makes VPNs the perfect tool for committing click fraud. So, how do VPNs work, and how are they used by fraudsters to commit click fraud and ad fraud?
What exactly is a VPN?
The virtual private network (VPN) is a piece of software that can be either downloaded as a standalone program or installed as a browser plugin. Popular, well-known VPNs include NordVPN, ExpressVPN, and Hola. The VPN market has grown exponentially over the past 10 years as consumers and businesses seek to protect their data and secure their privacy, generating more than $15 billion in revenue. Europe and North American VPN use is at 17 percent, while 25 percent of internet users now use a VPN, with the highest use in Asia Pacific and Latin America.
As the name suggests, they create a virtual location for you, using a unique new IP address every time the VPN is activated.
Using the VPN and the new IP address, you can then choose how your location is presented online. So, if you’re in India, for example, you could use a VPN to show your location as the USA.
This works by routing your traffic through the VPN’s servers or network so that it doesn’t show as coming from your own location.
A common reason to use a VPN is to get around location restrictions on websites or national firewalls.
An example of popular and legitimate use for VPNs is to access blocked social media sites such as Facebook in China.
Or for users of streaming services that are only available in their home country (for example, the BBC iPlayer video streaming is only available in the UK). Or to watch Friends from wherever you are.
Many of them are subscription-based, but there are many free VPNs that use a peer-to-peer functionality.
Tor Network (“The Onion Router”)
In a similar vein, Tor is software designed to provide users with anonymity and security in some online communications. It also allows them to access certain websites and services on the Deep Web. The U.S. Naval Research Laboratory actually developed the core concept of sending communications anonymously and securely. Later, a group of researchers (with the Navy’s permission) created the Tor Project, which provided free and openly accessible software for private parties and other government agencies to enhance the anonymity and security of their communications. The term Tor derives from the acronym of “the onion router (Tor))” which metaphorically compares the layers of an onion to the way in which the network provides layers of encryption to communications. Like the VPN, this can be used for completely legitimate reasons. However, it is also a common method of proxy traffic fraud.
VPNs used for fraud
You’re probably already seeing how a VPN, or the Tor browser can be a useful tool for internet fraud, especially PPC fraud. A VPN works by routing the device internet connection through a chosen VPN’s private server rather than the internet service provider (ISP). When data is transmitted to the internet, it comes from the VPN rather than the device. Fraudsters abuse this tool to mask their operations and hide their IP addresses to avoid being blacklisted. This tricks advertisers into thinking that their engagement originated from desired locations. With emulators, VPN proxies, and other technological tools borders become irrelevant, allowing fraud to easily infiltrate any country.
With Pay Per Click (PPC) advertising, marketers often target a specific locale to ensure they’re getting the best value for money on their ad campaign.
By using a VPN, a web user can create a new ‘virtual’ IP address and use this to mask their true location.
This type of location obfuscation is often used wholesale by organised setups such as click farms or botnets. With a bank of servers pre-loaded with VPNs, fraudsters can route bot traffic or click farmers through these IP addresses to send bulk clicks from wherever in the world they want. Based on billions of impressions analysed for enterprise clients, CHEQ For PPC has found that more than one in five invalid clicks (21%) include location obfuscation, via emulators, VPN proxies, and other cheats.
For casual click fraud too, a VPN can be simple yet effective. A local business rival just needs to download a VPN onto one or two devices, and they can wreak havoc with a pay-per-click (PPC) campaign.
In countless click fraud prevention strategies for our clients, we have found the devastating effect of location obfuscation:
- A top skin care brand spending hundreds of thousands of dollars on PPC spend suffered from malicious VPN and data center traffic. In fact, 95% arrived from data centers, and 5% from proxy/VPN based on users who were “out of Geo” and would not have been included in the client’s campaign targeting. This led to $80,000 in savings, reinvested in safe inventory.
- One of the world’s largest DIY marketplaces spending $ 2.5 million a month, particularly on Google Paid Search, saw more than 14,000 invalid clicks a month with users deploying a VPN to mask their location, primarily from China and Malaysia (masking their location as UK buyers). This is considered invalid by the client as they do not ship to these regions.
In short, the VPN is an effective click fraud tool that can be very hard to spot or stop.
How to spot VPN traffic
OK, so yes, it is hard to spot VPN traffic, but in fact, VPN click fraud can be stopped quite effectively if you know how.
Even by masking its true location, a VPN will leave a footprint.
These are some of the most common and effective ways to spot VPN traffic on your PPC ads.
IP address fraud scores
With all those generated IP addresses, being able to rank and score the likelihood of fraud is very useful. There are IP address checkers that can tell you how likely fraud is on a suspect address.
Device IDs
Click fraud prevention software actually assigns unique identifiers to devices, not IP addresses. This means that even if a device is using a VPN to change its IP address multiple times, it will always be identified by the software.
This is a common problem with the PPC platforms approach to click fraud prevention, where they focus on the IP address instead of the device.
can make them harder to spot using this method, but even that can be a red flag in itself.
Is all VPN traffic fraudulent?
It might seem like anyone committing click fraud or ad fraud is going to use a VPN to do it. And this makes sense, as it helps them to cover their tracks.
But, if you’re wondering if every click from a VPN on your paid ads is click fraud, well… Probably not.
Some people just use VPNs to maintain their privacy online. Others might be using a VPN to get around those location restrictions, as we mentioned before. Perhaps they want to look up a service or product from home while they’re on vacation.
So, although most ad fraud traffic will use VPNs, not all VPN traffic is fraudulent.
Again, using intelligent software, such as a free trial of CHEQ, can help to differentiate between the two.
P.S.
Want to protect your sites and ads? Click here to Request a Demo.