Online fraudsters have to be stealthy if they want to get away with ad fraud, form jacking, web scraping, or other malicious actions. In order to overcome the multiple security checks that many websites have in place, these bad actors must mimic the behaviors of legitimate site visitors.
One of the most popular ways for fraudsters, botnets, and hackers alike to do this is to use a proxy, which allows them to disguise their true identity and pose as harmless traffic from another, less suspicious server or geolocation.
But proxies are not inherently malicious. Just as real users may disable javascript, real users will also often use proxy services or VPNs to protect their privacy online.
So, how can businesses tell if a proxy user on their site is a legitimate visitor or a fraudster? The first step is understanding what proxies are, how they work, and how to detect and block invalid proxy traffic.
In this article, we’ll cover what proxies are, explain different types of proxy traffic, how fraudsters use it, the threats proxy traffic can pose, how you can determine whether or not proxy traffic is invalid, and how you can protect your go-to-market initiatives from invalid proxy traffic.
What is a Proxy?
A proxy is a tool designed to act as a middleman between devices. The proxy has its own IP address, which allows the user to obfuscate theirs, allowing them to mask their identity and location.
Proxies are used for many reasons, such as filtering web content, avoiding regional restrictions or gaining access to content from another country, screening downloads, and providing anonymity. Certain kinds of proxies, like Virtual Private Networks, are also frequently used in the business world to provide a secure gateway to corporate networks.
But, as you can imagine, proxies are also an invaluable tool for fraudsters and other bad actors, as they can be leveraged to mask fraudulent and malicious behavior, making it much harder to track and react to. For example, one popular use case is the automated use of a proxy in click fraud attacks, in which the IP address is repeatedly changed to mimic multiple users clicking an ad in rapid succession.
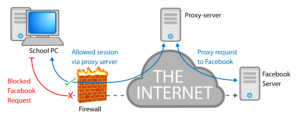
Wikipedia: A proxy server allows access to blocked content.
Three Kinds of Proxies
There are many different kinds of proxy servers–forward proxies, transparent proxies, data center proxies–the list goes on. But these can generally be divided into three categories: Virtual Private Networks (VPNs), web proxies, and content delivery networks (CDNs).
Virtual Private Network (VPN)
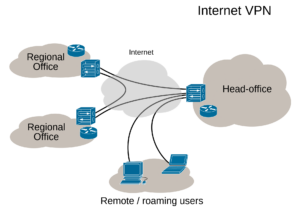
A Virtual Private Network (VPN) is a common type of proxy that routes all network traffic to and from a device through itself and typically encrypts that traffic. You can imagine a VPN as an encrypted tunnel, through which all incoming and outgoing traffic is secured. VPNs are frequently used by both privacy-conscious users, and businesses looking to secure traffic to and from their network, but they’re also leveraged by bad actors looking to anonymize their traffic, and by Tor exit nodes.
Web Proxy
A web proxy, or public proxy, is a server that is leveraged to provide a gateway between a user and the broader internet. The proxy has its own IP address, which your computer knows, and when you send traffic to the internet, it is routed through the proxy, which gets a response from a web server, and then routes that data back to your browser.
There are both hardware and software web proxies, with hardware proxies being actual physical servers sitting between your network and the internet, while software proxies are typically hosted by a cloud service provider.
Content Delivery Network (CDN)
A Content Delivery Network (CDN) is essentially a group of proxy servers distributed across the internet with the goal of providing better availability and performance than singular servers. CDNs are an extremely widespread tool for legitimate business purposes, for example, website owners who have visitors in multiple geographic locations can leverage a CDN to enable faster delivery of content. But they can also be hijacked for malicious purposes, such as the delivery of malware.
How Do Malicious Users Leverage Proxies?
The most common use for proxies, malicious or otherwise, is simply to hide the user’s location and identity. However, sophisticated attackers can leverage the technology for complex use cases, often to devastating effect.
For ad fraud purposes, servers with VPNs can be used to reroute traffic from click farms and botnets through rapidly changing IP addresses, allowing them to mimic legitimate clicks.
Proxies can also give fraudsters access to desirable regions with higher PPC costs, such as North America or Europe, where there’s typically a higher cost per click and, therefore, a higher reward for fraud.
The level of sophistication can vary, with some uses simply spoofing a US IP address and others using complicated residential proxies to fake other details, such as network or device. For example, a headless browser originating from southeast Asia could masquerade as a mobile device with a 5G connection in the United States.
From a business standpoint, even casual proxy use by legitimate users can be problematic. Proxies and VPNs skew marketing data, disrupt browser fingerprinting, and prevent remarketing efforts.
Is All Proxy Traffic Invalid?
As mentioned above, there are many legitimate reasons to use a VPN or a proxy, and there are millions of users using these tools on a daily basis, both for privacy and business reasons.
In order to properly categorize proxy traffic and protect your website from malicious proxy traffic, it’s best to categorize activity that comes from a questionable or unidentifiable source as suspicious rather than blocking it outright. There are many reasons why someone might want to mask their identity online. The intentions could be harmless, but if that user has no chance of converting because of the barriers in place, then you’ll probably want to either monitor or potentially block this traffic. It is also important to keep in mind that even if anonymous traffic isn’t malicious, it can still skew campaign data and provide misleading information.
How to Detect and Block Proxy Traffic
So how can marketers detect and block proxy traffic?
To start, it’s best to determine if proxy traffic is malicious and should be blocked or if it’s simply suspicious traffic. When we analyze customer traffic, we follow a series of best practices to determine what action should be taken and how to best respond to proxy traffic. Of course, these steps are easier with a comprehensive go-to-market security platform, but they can be undertaken manually, with considerable time and effort.
Monitor Site Traffic
First, it’s important to closely monitor the customer domains accessing your page. If you are receiving a high volume of clicks from unusual locations, that’s a good sign that your site or your advertising campaigns are being targeted. Once you’ve noticed high volumes of anomalous traffic, it’s time to search your server logs for suspicious IP addresses and add those addresses to your blocklist or the blocklists of your advertising partners.
Inspect Packet Headers for Suspicious Data
Technically adept users can also inspect packet headers for corroborating information. These headers can contain a lot of information, such as browser type and version and OS. If you receive a lot of requests from the same IP address but notice a different browser or OS each time, there is a high probability that this IP is a proxy and can be blocked or redirected, depending on your industry and use case. If you want to allow proxy users to access your site but want to keep malicious users out, you can look for giveaways such as Linux use or the use of outdated browsers and narrow the scope of your blocking.
Look for Misrepresentation
To take things a step further, find areas where the user misrepresents themselves. For example, if a user appears to be using a mobile device, but the packet header reveals browser extensions on that device, it’s safe to assume that the user is falsifying one or more pieces of information since mobile devices do not utilize browser extensions.
All of these pieces of information can be combined to help determine whether proxy traffic has malicious intent or is simply a privacy-conscious user and to adjust your blocklists accordingly.
Consider Comprehensive Go-to-Market Security
If the above seems like a heavy lift–that’s because it is. Manually mitigation is possible, to a certain extent, but it’s extremely time-consuming, even when leveraging external proxy blocklists and tracking scripts to identify bad traffic.
For businesses serious about security, a comprehensive go-to-market security platform will help automatically detect and block invalid traffic and provide additional insight into marketing analytics.
Our platform, CHEQ, leverages thousands of security challenges to evaluate site traffic in real-time, determine whether a visitor is legitimate, suspicious, or invalid, and take appropriate action to block or redirect that user. Book a demo to see how CHEQ can help you lower your CPA and protect your go-to-market efforts against invalid proxy traffic and other forms of fake traffic.