Your pay-per-click (PPC) ads are getting tons of clicks… that’s a good sign, right?
Don’t pop the champagne bottle yet.
40% of internet traffic is invalid, consisting of botnets, scrapers, crawlers, click farms, fake accounts, and other forms of invalid traffic (IVT). It can negatively impact your marketing funnel, paid marketing efficiency, on-site conversion rates, and analytics accuracy.
In fact, ad fraud (or click fraud), including competitor click fraud, cost marketers $42 billion in 2021. If you don’t take the right steps to protect your business from IVT, you could spend a lot on online ad campaigns without generating the expected results.
Here’s what you need to know about competitor click fraud and how to detect it to protect your business from losses.
What Is Competitor Click Fraud?
Competitor click fraud occurs when a rival business clicks on your online ads (e.g., on Google Ads paid search results) to send IVT to your website.
While competitor click fraud can affect any business and sector, the eCommerce/retail industry is amongst the hardest hit — incurring a $3.8 billion loss to click fraud in 2020.
Additionally, IVT can pollute your audiences and skew your look-a-like models and automation pixels — decreasing the effectiveness of your overall go-to-market (GTM) strategy.
Why Do Competitors Commit Click Fraud?
The ultimate goal of competitor click fraud is to cost you money and decrease your ability to compete for ad placements. Unscrupulous competitors commit click fraud to drive up the amount you pay for a search term while depleting your PPC ad budget with irrelevant clicks. When you have less money to spend on driving legitimate traffic, you become less competitive and may get pushed out of the market.
How Does Competitor Click Fraud Work?
Competitor click fraud is more than just your rivals clicking on your online ads whenever they see them to cost you a few dollars here and there. While manual click fraud does occur, most commonly for small businesses, most large-scale competitor click fraud operations utilize sophisticated automated and outsourced methods to evade detection and cause more extensive damage.
In-house Clicks
As noted above, manual click fraud is typically a small business concern. For example, one contractor may purposely click on another’s ad when they are competing for the same listings, and because small business advertising budgets are typically small, it’s possible to fully deplete a PPC budget in this manner. However, there are outlying cases of organized manual click fraud on a greater scale. For instance, a company may have employees from multiple departments and locations click on their competitors’ ads. Even though you won’t find an initiative called “sabotage our rivals” in their marketing plan, there’s often an unspoken understanding baked into the company culture to perpetuate the behavior.
Click Farms or Bot Farms
For companies unwilling to do the dirty work themselves (and with extra budget for fraud) there’s an entire industry based on providing click-fraud-as-a-service. These businesses let your rivals outsource click fraud to click farms, teams of thousands of human workers who purposefully and repeatedly engage in advertisements with no intention of converting. These click farms often market themselves as ‘engagement boosters,’ but click fraud is at the heart of the business model.
Direct revenue schemes, or PTC (paid-to-click) sites, are booming. These services pay tens of thousands of people to click on ads. The business model of PTC sites is generally based on profiting from advertisements clicked on by visitors. Scarlet Clicks, one of the larger Pay-to-Click players, pays workers fractions of a penny per click and claims over one million members. Scarlet Clicks charges ‘advertisers’ a mere $1.50 per 1000 clicks, a volume that can easily cost hundreds in PPC budget.
Click Bot Software
A competitor can also purchase software for committing click fraud — often for less than $200 a month. These apps vary in sophistication, but at a minimum they usually leverage proxies or VPNs to mimic diverse traffic by constantly switching IP addresses to evade detection. Some click bot providers, like TrafficBotPro.com, even boast that they can overcome bot mitigation based on browser fingerprinting and falsify user actions like mouse and scroll patterns to fool reCAPTCHA.
Botnets
For technically savvy competitors willing to DIY their click fraud, a botnet can be a cheap and effective way to carry out the attack. A botnet is a network of internet devices that have been hijacked by malware to perform a specific task. While most people think of botnets as large and high-profile tools used by sophisticated hackers to carry out DDoS attacks, the truth is that botnets are surprisingly easy to put together. Just search ‘rent a botnet’ on Google, and you’ll get millions of results. A competent bad actor can build a basic botnet in less than an hour, and there are plenty of tools, online vendors, and builder kits available to help expedite the process.
The benefits of using a botnet for click fraud are immense: because the invalid traffic is coming from thousands of different ‘real devices,’ it’s much harder to detect a pattern and identify the fraud. Browser fingerprinting or user behavior analysis can help overcome this challenge, but sophisticated botnets often have built-in defenses against such techniques.
How To Detect Competitor Click Fraud
If you suspect that your PPC campaigns are sabotaged, perform these manual checks to identify fraudulent clicks:
Check IP Addresses
Analyze your website visitor log to see if there are frequent and suspicious clicks from the same IP addresses or locations your campaigns don’t target. If you detect a pattern of repeated clicks from the same IP address, that is likely an instance of basic manual click fraud and can easily be mitigated by blocking the IP or adding it to your ad platform’s exclusion list. High volumes of clicks from regions or timeframes outside of your business’s reach are also a good indicator of invalid traffic.
Review Your Publisher List
Review your publisher list to see if your ads are channeled onto PTC sites. Go to Google Ad’s placement section and look for high-traffic, suspicious websites. Telltale signs of PTC sites include pages covered in ads with sparse and irrelevant content and recently registered domains.
Monitor Campaign Activities
Search your campaign log for suspicious timings or spikes in the number of clicks that don’t result in engagement with your content while showing high bounce rates. Also, traffic from suspicious devices and custom browsers may indicate fraudulent activities.
Identify Patterns
If you suspect you’re a victim of click fraud, you’re probably not alone — your competitors may be under attack as well. You can team up with other local retailers to compare notes and identify patterns to get to the bottom of the issue.
How To Stop Competitor Click Fraud
If you have concluded that you may be a victim of competitor click fraud, you can take actions to mitigate click fraud manually by making your PPC campaigns more airtight:
- Set up IP and ISP (internet service provider) exclusions.
- Redirect your ad budget to remarketing campaigns, which only target people who have shown interest in your products or services.
- Exclude locations, languages, demographics, and devices where suspicious clicks originate from your targeting.
- Set your ad campaigns to run only on reputable, high-value sites.
However, there’s only so much you can do manually. Tracking down suspicious activities is costly and time-consuming. Not to mention, you’d have already suffered losses by the time you spot suspicious activities.
The good news is that you don’t have to go it alone. You can use fraud protection software to help you detect and block suspicious activities before they put a dent in your ad spend.
For example, CHEQ’s Intelligence Engine runs over 2,000 real-time security challenges on every online visit. When a suspicious IP address, device, or VPN is identified, it’ll automatically be blocked.
CHEQ will help you continuously identify suspicious traffic sources with these three components:
- A Bot Mitigation engine uncovers and blocks invalid bot activity using advanced fingerprinting methods and a multi-layered security model.
- A User Validation engine performs real-time browser tests to root out visitors attempting to mask their identities.
- A Behavioral Analysis engine detects anomalous activity at both the network and the individual level.
Blocking IVT means you can spend your budget on driving high-quality traffic to maximize revenue opportunities. You can also clean up your data to inform accurate audience segmentation and targeting for future ad campaigns.
Learn more about CHEQ and book a demo to see how we can help you secure your paid marketing.
Over the past 40 years, the internet has expanded into a massive highway of information–with billions of daily active users and trillions of daily engagements–driving innovation, growth, and connectivity on a global scale.
But as the internet has grown in scale and sophistication, the quality and authenticity of its traffic have decreased as the web is increasingly flooded with automation tools, bots (good or bad), and users who, for one reason or another, aren’t genuine. In the marketing industry, this traffic is known as Invalid Traffic (IVT).
To help better understand this phenomenon and the impact it has on businesses, CHEQ has conducted the first annual State of Fake Traffic report.
By analyzing billions of data points from tens of thousands of anonymized campaigns, funnels, and websites protected by CHEQ, we were able to gain accurate insights into the scope of the fake traffic problem and how it affects different platforms, industries, and regions. In this blog post, we’ll examine the leading referral sources for fake traffic in an effort to show which platforms are leading sources of bot traffic. For more information on how specific industries, regions, and platforms are affected by fake traffic, download the full 35-page report here.
What is Invalid Traffic (IVT)?
Invalid traffic is web traffic that consists of bots, fake users, and otherwise invalid users who cannot turn into legitimate customers. This could mean harmless bots like search engine web scrapers or malicious traffic like ad fraud botnets.
Google defines invalid traffic as “any activity that doesn’t come from a real user with genuine interest. It can include accidental clicks caused by intrusive ad implementations, fraudulent clicking by competing advertisers, advertising botnets, and more.”
To Google, IVT is primarily a concern because it can be used to artificially inflate a publisher’s ad earnings, a practice that is against Google Ad’s terms of service. But invalid traffic isn’t limited to paid traffic; it also makes up a large portion of direct traffic and unique site visitors and has plenty of adverse effects downstream, from polluted marketing analytics to wasted remarketing efforts.
Invalid Traffic’s Impact on Marketing Organizations
Historically, IVT has been a major concern for information technology and security teams looking to guard organizations from bad actors disguising their online footprint to commit attacks. However, as today’s CMOs have realized, IVT is also a prevalent problem for marketers and go-to-market teams.
For marketers and businesses dependent on web traffic to drive sales, this creates a unique challenge: Because of the prevalence of IVT, nearly every marketing funnel, campaign, and operation is impacted to some degree, oftentimes in very harmful ways.
Where IVT is present, audiences, CDP segments, and CRMs become polluted, campaigns become optimized toward fake users, and revenue opportunities are missed. Analytics and BI systems are skewed by bad data, leading to poor insights and worse decisions made on bad information.
Additionally, website and conversion funnels are disrupted by invalid leads and visitors. This is a challenge that must be dealt with, sooner, rather than later.
Examining Invalid Traffic by Source
Fake traffic is a persistent threat that affects all digital marketing channels. Left unaddressed, this fake traffic will waste advertising budgets and create negative downstream effects such as poorly optimized and ineffective campaigns, confused analytics, and inaccurate attribution.
Despite the best efforts of search engines, ad networks, and social media platforms to mitigate fraud and falsification through dedicated teams and built-in tools, there remains a significant ingress of fake traffic across all platforms.
Our analysis of billions of fake traffic referrals found a general level of parity in fake traffic across most platforms, with some notable exceptions. The general findings of our research is outlined in the chart below:
Social Fake Traffic Rates Climb as Professional Networks Attract Bad Actors
While the general fake traffic rates for social media platforms were lower than comparable search and display ads, one category of social media had, by far, the highest fake traffic rates of any platform studied.
Professional networking platforms had an average invalid referral rate of 12.4%, with 9.7% of paid traffic and 15.3% of organic traffic determined to be invalid.
For hackers, these platforms make a convenient group of high-value targets.
For those committing ad fraud, the incentive is even stronger. At an average of $5.58 per click in 2022, the cost-per-click for professional networks is typically up to five times that of typical social and PPC costs. From an attacker’s point of view, that makes it five times more efficient to target a campaign on these sites.
Click Hijacking Attacks Drive Fake Traffic to Display Ads
Display ads are the oldest form of online advertising, and they’re still an extremely effective tool that allows businesses to reach a broad audience and raise brand awareness. However, because these ads are delivered to third-party websites, they are often easily manipulated by malicious actors. Display ads are particularly vulnerable to clickjacking attacks, which grew by 125% across all platforms in 2022.
This deluge of these attacks lead to a fraud rate of 7.2% for displays in 2022, 40% higher than the rate for search ads.
Click hijacking occurs when a valid user clicks on an asset, such as a link or advertisement, that appears to be legitimate, but it is actually a disguised malicious element, which may install malware, or redirect users. Last year, researchers discovered a set of Google Chrome extensions that had been installed over one million times was hijacking searches and inserting affiliate links into web pages, disrupting user experience, and costing retailers thousands in affiliate fraud. In the case of a display ad, an attacker may use various techniques, such as adding hidden layers or modifying the code of a webpage, to cause a display ad to be clicked without the user’s knowledge. The attacker can then collect payment for the fake click from the advertiser.
This type of attack can be difficult to detect and prevent because it occurs on the client side, and the user’s browser is often not able to distinguish between a legitimate click and a hijacking click.
Viewbots Inflate Streaming Numbers and Burn Advertising Dollars
Streaming platforms had an unprecedented reach in 2022. The top streaming site reaches more people aged 18-49 than all TV networks combined, and it reaches them with more ads–which are statistically more likely to hold viewer attention, and ultimately to convert.
But many of those ad viewers are not human. In 2022, streaming platforms generated the highest invalid rate for paid traffic of any category, at 11.1%. Based on the ad revenue figures of just one streaming platform, that could amount to over $3 billion in wasted ad spend.
So where is all of this traffic coming from? The answer is view bots, a relatively new form of fake traffic in which pieces of automated software (bots) are used to view streaming videos or live streams in order to artificially boost the view count and generate fake engagement–and fake ad views–for unscrupulous creators.
Most view bots are simple scripts that open a video in a headless browser, but more complicated viewbots may also create fake accounts to mimic logged-in viewers, and can even incorporate a chatbot capability that will spam the stream’s chat or comments section with artificial banter to make audience numbers appear more legitimate. Some viewbots will even click through on ads to increase the perceived click-through rate. And these bot networks are available for rent for prices as low as $10/month.
The impact of these fake viewers goes far beyond fake clicks–most established creators offer partner programs, where they earn a commission for mentions or ad impressions.
If those impressions are generated by bots, not real people, then the ad budget used to create and place those ads has essentially been wasted.
If it costs $2000 for 100,000 impressions, and 15-20% of those impressions are fake, that’s $150-200 wasted. Considering most advertising campaigns on these platforms measure impressions in the millions, the costs of those fake impressions can add up fast. Furthermore, with key performance metrics becoming skewed by fake traffic, decision making becomes increasingly difficult.
Get All the Details in the State of Fake Traffic Report
Want to know more about the state of fake traffic in 2023? Download the full report here to get a full overview of fake traffic threat groups and types, how fake traffic breaks down across traffic sources, and more
In this 35-page report, we offer new insights into invalid traffic trends and statistics as we:
- Share invalid traffic rates and trends
- Examine prominent and growing threat types
- Compare invalid rates across 11 major industries
- Compare invalid traffic by region of origination
- Compare invalid rates for paid and organic traffic generated by leading ad platforms, search engines, and social media platforms.
Download our free report today and learn about the latest trends and insights in the world of invalid traffic.
About the author:
This post was written by Yoel Israel, the CEO of Wadi, the leading digital agency that specializes in digital marketing for cybersecurity brands, and Cyfluencer, a content-sharing platform for cybersecurity vendors & influencers.
Cybercriminals are an increasing concern for companies worldwide. Cyber-attacks have become a popular way for criminals to extort money, steal company data and secrets, disrupt operations, and tarnish brand reputation. While many companies prioritize revenue-generating investments during harsh economic times, modern cybersecurity systems are necessary to protect revenue, trade secrets, and brand image.
Companies can be most vulnerable to cyberattacks during a Go-to-Market (GTM) strategy. Since GTM strategies are costly, time-consuming, and vital to achieving revenue goals, any disruption to a GTM strategy can be devastating. By understanding the top cyber security threats that affect GTM strategies, you can build up your company’s defenses and protect your investments.
What is a Go-to-Market Strategy?
A Go-to-Market strategy (GTM) is an action plan that outlines how a brand will reach target customers, launch new products or services, implement new strategies or systems, or achieve other business goals.
Companies use GTM strategies to create comprehensive timelines that communicate to stakeholders the step-by-step process, desired outcomes, and how to measure success.
There are numerous benefits to creating GTM strategies:
- Reduces time to market for products and services.
- Outlines plan and responsibilities for internal and external stakeholders
- Improves probability of success
- Mitigates risk for additional costs
- Implements scalable solutions for business growth
- Allows for strategy adaptions
- Ensures positive customer experience
With GTM strategies, brands can create organized systems and structures that reduce operational costs and increase the probability of success.
The Top Cyber Threats Facing GTM Organizations
GTM strategies provide companies with a valuable framework to bring new products, services, systems, and structures to life. While GTM strategies already have inherent risk factors, cyber threats can cause detrimental harm to businesses.
To avoid cybercrimes, companies should understand the various threats they face and how to avoid them.
1. Bots
Bots are a popular tool for many web developers to improve customer experiences. However, cybercriminals can easily create malicious bots to harm your operations.
Cybercriminals will create a network of bots to overwhelm security systems and disrupt digital operations such as websites, servers, payment systems, etc.
GTM strategies are at risk from bot attacks because they generally rely on precision timing and increased operational capacity.
For instance, a business launching a new product may expect 10x the regular web traffic. Bot attacks can cause websites to shut down, payment systems to malfunction, and other technical difficulties. This can diminish the effectiveness of a product launch, negatively impacting ROI and business growth.
To stay prepared, companies should understand the different types of Bot attacks:
Form Bots
Form-filling bots are typically programmed to use stolen customer data to fill out forms and defraud, disrupt, or manipulate companies by providing useless or misleading data.
Account Takeovers
Account takeovers will use bots to access a company’s bank info, payment info, or other information to gain unauthorized access or create fraudulent transactions.
DDoS Attacks
Distributed denial-of-service (DDoS) attacks use bots to overwhelm websites, servers, and digital systems with fake traffic to shut down servers and cybersecurity systems to gain access to valuable information.
2. Ad Fraud
Ad fraud is another style of attack companies may encounter where cybercriminals use bots and malicious software to gain information, mislead companies, or disrupt operations.
Cybercriminals can use ad fraud tactics to scam companies out of marketing spending and limit operational functionality. These tactics can negatively impact any GTM strategy by wasting company time, money, and other resources.
Companies should understand the types of ad fraud scams to stay vigilant:
Ad Injections
Cybercriminals use Ad injections to replace existing ads with their own through malicious software. These fraudulent ads can carry malicious software, disrupt company websites, or advertise without paying.
Cookie Stuffing
Cookie stuffing is a form of affiliate marketing fraud. Companies will pay out advertisers and other websites that send users to their websites. However, cybercriminals can use cookies to gain commission without the company gaining any real traffic.
Click Spam
Similar to ‘Cookie Stuffing,’ click spam is when a cybercriminal fakes clicks to receive a commission from a company.
3. Client-side Attacks
Client-side attacks are when companies download malicious content that allows hackers access to company systems and data.
Client-side attacks are initiated by users within a company that takes the bait from hackers. The best way to defend against these attacks is to educate employees to watch out for malicious links, downloads, and other harmful software that could initiate a client-side attack.
To protect your operations and GTM strategies from Client-side attacks, companies should be aware of the following tactics:
Web Skimming
Web skimming is when an attacker injects malicious code into a website to gain information from a user. This information is then sent to a server that the hacker controls.
Formjacking
Formjacking is when cybercriminals use malicious code to take over the functionality of a site’s form page to collect information like login credentials, payment info, and more.
Cross-Site Scripting (XSS)
XSS attacks are when hackers inject malicious software into a company’s website to go after customer information. Cybercriminals will target seemingly safe websites that customers where customers wouldn’t expect a hack to occur.
4. Consumer Data Risks
When companies don’t implement the right cybersecurity measures, the risks go beyond lost data and disruptions to GTM strategies.
Customers who suffer from a data leak or scam by using your website will lose trust in your company. Further, by allowing cybercrimes to affect your customers, you can open your business to certain fines and litigation.
Companies should be aware of these risks when creating a GTM strategy:
Brand Reputation
Customers who become victims of fraud and data leaks are less likely to trust that company. The effects on brand reputation can last years and weaken any upcoming GTM strategy.
GDPR Fines
Many governments, like the UK, impose fines on companies for allowing data leaks and cyberattacks to take place. Failing to protect your customers can cost your company up to 4% of its annual revenue or more.
How to Protect Your Revenue with Go-to-Market Security
Investing in cybersecurity systems is the best way to protect your GTM strategy.
Software like CHEQ provides companies with tools and strategies to help reduce risks and let companies focus on their GTM strategy. CHEQ’s GTM security software secures data, scans for bots, ensures user authenticity, and blocks suspicious browsing patterns.
Securing Your Bottom Line
Cybersecurity has never been more critical as companies rely on e-commerce sales and digital capabilities to engage customers and grow their brands. By investing in cybersecurity systems, companies can reduce their exposure to cybercrimes and protect their customers and profit margins.
Companies should take special care in their cybersecurity when launching a GTM strategy. During these times, companies are the most vulnerable to attacks. Using tools like CHEQ’s GTM security software, organizations can ensure the success of any GTM strategy.
If you have implemented multiple security checks to fend off invalid website traffic but are still plagued by fraudulent clicks — you’re not alone.
Many bad actors circumvent these measures by using IP masking techniques to disguise their identities, pose as harmless traffic from unsuspicious sources, and mimic the behaviors of legitimate visitors.
Here’s what you need to know about IP masking and how to identify and protect yourself from such fraudulent traffic.
What is an IP Address?
IP stands for internet protocol, which transmits data across the internet. Each device connected to the internet has a unique IP address to enable two-way communication between clients (e.g., a web browser) that ask for data and servers that respond to the requests.
The IP address tells the server who makes the request and where to send the information. These activities are often tracked for various purposes, such as informing online ad targeting to help marketers deliver the most relevant content to people with high purchase intent.
An IP address also works as a unique identifier, like a fingerprint. It can help authorities track down the source of malicious activities in a cyberforensic investigation. As such, fraudsters and malicious bots often use IP masking techniques to evade detection.
What is IP Masking?
IP masking hides or replaces an IP address with a different one. It enables users to preserve anonymity, making it harder to identify their locations or associate their identities with their web activities.
Why Do Users Mask Their IP Addresses?
There are many legitimate reasons for web users to mask their IP addresses — primarily to preserve privacy and anonymity:
- Keep physical addresses private
- Stop companies from collecting personal data
- Prevent Internet Service Providers (ISP) from tracking their online activities
- Keep online search history private
- Avoid malicious or intrusive ads
- Subvert censorship and geo-blocking to access restricted or copyright-blocked content in certain countries
Why Do Bots and Bad Actors Mask Their IP Addresses?
Fraudsters abuse IP masking to hide their identities when conducting illegal activities, such as ad fraud, form jacking, and web scraping, by mimicking the behaviors of legitimate site visitors to evade security checks.
Bad actors change the IP address of traffic from click farms and botnets to make it look like the clicks are coming from multiple sources instead of a single location. They also alter their IP addresses to regions with higher PPC costs to achieve a higher reward for fraud.
Additionally, criminals can use IP masking to circumvent IP blocking or filtering to carry out a distributed denial-of-service (DDoS) attack against websites to create massive service disruptions.
How Bots and Fraudsters Mask Their IP Addresses
Bad actors can apply various techniques to mask their IP addresses. Here are some common methods:
Residential Proxy Networks
These proxy networks contain real IP addresses from ISPs and are associated with less suspicious physical locations. Fraudsters route their traffic through proxy servers to disguise visits and clicks from their bots as legitimate traffic.
Virtual Private Networks (VPNs)
A VPN creates a virtual location with a new, unique IP address every time it’s activated. It can make internet traffic appear to originate from different geographic locations by routing it through a global network of servers.
Click farms or botnets often set up VPNs to send bulk clicks. CHEQ For PPC analyzed billions of impressions and found that 21% of invalid clicks involve location obfuscation.
Botnets
Fraudsters can control random, geographically dispersed devices by infecting them with malware without the owners’ knowledge. Then, they route traffic through these devices to mask their locations and identities.
Since the traffic comes from individual IP addresses that aren’t suspicious in and of themselves, it’s much harder to stop these fraudulent activities. Plus, even if you block one of the IP addresses, fraudsters have thousands more they can exploit.
TOR and Anonymous Browsers
Tor is a free network that conceals the identity and origin of a web user by using multiple relay nodes. Each node only knows the IP addresses before and after it. Even if the traffic is intercepted, parsing through the data to uncover the originating IP address will be very challenging.
How to Detect IP-Masked Traffic
For marketers, ad fraud is the biggest headache caused by IP masking. Fraudsters can reroute traffic from click farms and botnets to mimic legitimate clicks. They can also make the clicks appear to come from locales with higher PPC costs (e.g., North America or Europe) to deplete the victim’s ad budget.
Here’s how to detect IP-masked traffic:
Monitor Site Traffic
The first step to fighting IP-masked traffic is to track domains accessing your site. Your site or ad campaigns may be targeted if you see many clicks coming from suspicious locations. You can analyze your server log to uncover and block suspicious IP addresses.
Use Multiple Identifiers
However, relying solely on IP addresses to identify invalid traffic could cause you to block good traffic along with the bad while missing fraudsters who use botnets or rapidly-changing IP addresses to carry out their attacks.
To one-up these bad actors, you must analyze numerous data points and use multiple identifiers such as device ID, browser type, and behavioral patterns to uncover fraudulent traffic.
Inspect Packet Headers for Suspicious Data
Packet headers that contain data on a packet’s contents, origin, and destination allow you to dig deeper into the technical aspect to find corroborating information, such as the browser type/version and OS associated with a request.
For example, if you see numerous requests from the same IP address with different browsers or OSs, the IP address is likely a proxy. You can further analyze users from that IP address to look for telltale signs like outdated browsers to avoid blocking legitimate traffic.
Look for Misrepresentation
You can take the sleuthing further to see if users deliberately misrepresent themselves. Those with malicious intent often falsify their data, and the insights can help you distinguish them from privacy-conscious visitors using VPNs.
For instance, if a request claims to be from a mobile device, but the packet header shows browser extensions (which don’t exist for mobile devices,) it’d be safe to conclude that the user is falsifying some of the data — and more likely to be carrying out fraudulent activities.
Consider Comprehensive Go-to-Market Security
If the above seems like a heavy lift–that’s because it is. Manually mitigation is possible, to a certain extent, but it’s extremely time-consuming, even when leveraging external proxy blocklists and tracking scripts to identify bad traffic.
For businesses serious about security, a comprehensive go-to-market security platform will help automatically detect and block invalid traffic and provide additional insight into marketing analytics.
Our platform, CHEQ, leverages thousands of security challenges to evaluate site traffic in real-time, determine whether a visitor is legitimate, suspicious, or invalid, and take appropriate action to block or redirect that user. Book a demo to see how CHEQ can help you lower your CPA and protect your go-to-market efforts.
Over the past decade, live streaming has gone from a niche platform for gamers to a cultural phenomenon and streamers have gone from microcelebrities to household names with follower counts surpassing the biggest names in Hollywood.
Twitch, the predominant live streaming platform, has grown from approximately 500,000 concurrent viewers in 2016, to over 2.76 million concurrent viewers in 2021, and amassed over 24 billion hours watched in 2021.
Those extraordinary viewership numbers have enticed other media giants to enter the market–YouTube, Facebook, and Instagram all now offer live-streaming capability.
In this online economy, views are money, and where money goes, fraud often follows.
In the shadow of the billion-dollar streaming industry is a booming marketplace for fake views generated by view bots and viewbotting services. These bots are cheap and easy to use, and for unscrupulous streamers, the reward often outweighs the risk.
What is viewbotting?
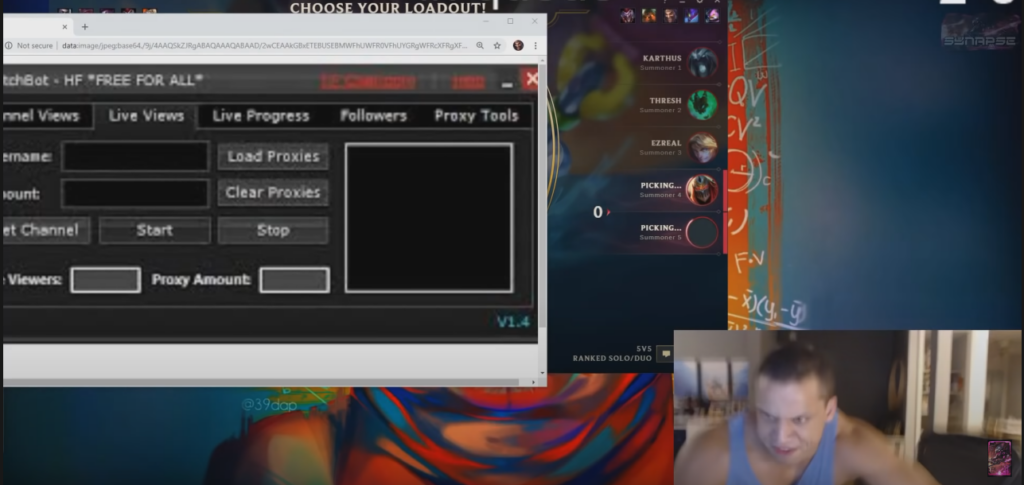
Viewbotting is a form of invalid traffic (IVT) in which pieces of automated software (bots) are used to view streaming videos or live streams in order to artificially boost the view count.
Most view bots are simple scripts that open a video in a headless browser, but more complicated viewbotting services may also create fake accounts to mimic logged-in viewers and incorporate a chatbot capability that will spam the stream’s chat or comments section with artificial banter to make audience numbers appear more legitimate.
Why do creators use View bots?
Alongside subscribers, views are one of the top metrics for success in the social media economy. Views determine whether a video is monetized on YouTube, where a video will rank in search results, and also act as a form of social proof–users are much more likely to click on a video that has lots of views.
Basically, the more views a YouTuber or Twitch streamer gets, the higher their earning potential.
To make matters worse, most streaming sites operate on the kingmaker system, promoting streams that have the most views and engagement at the top of their directories and search results. For newbie creators, this system can make it particularly difficult to break out and find viewership as they find themselves stuck streaming to small audiences, without any chance to be promoted by the algorithm.
With all of these factors in mind, it’s easy to imagine how tempting it can be for creators to use view bots to boost their viewership numbers and incite streaming platforms to promote their content.
It also doesn’t help that view bots are relatively easy to set up and use, and that it’s easy to have a layer of plausible deniability in using them, more on that later.
How does viewbotting work?
Most viewbotting is carried out either by viewbotting scripts that a user sets up themselves, or by paid viewbotting services that offer thousands of views for low prices. Let’s break it down.
Viewbotting scripts
Technically savvy streamers can easily write a script to run a headless browser to open a stream or video for a certain duration, thus creating a view. This can be scaled up by hosting hundreds or even thousands of instances on a cloud service such as AWS.
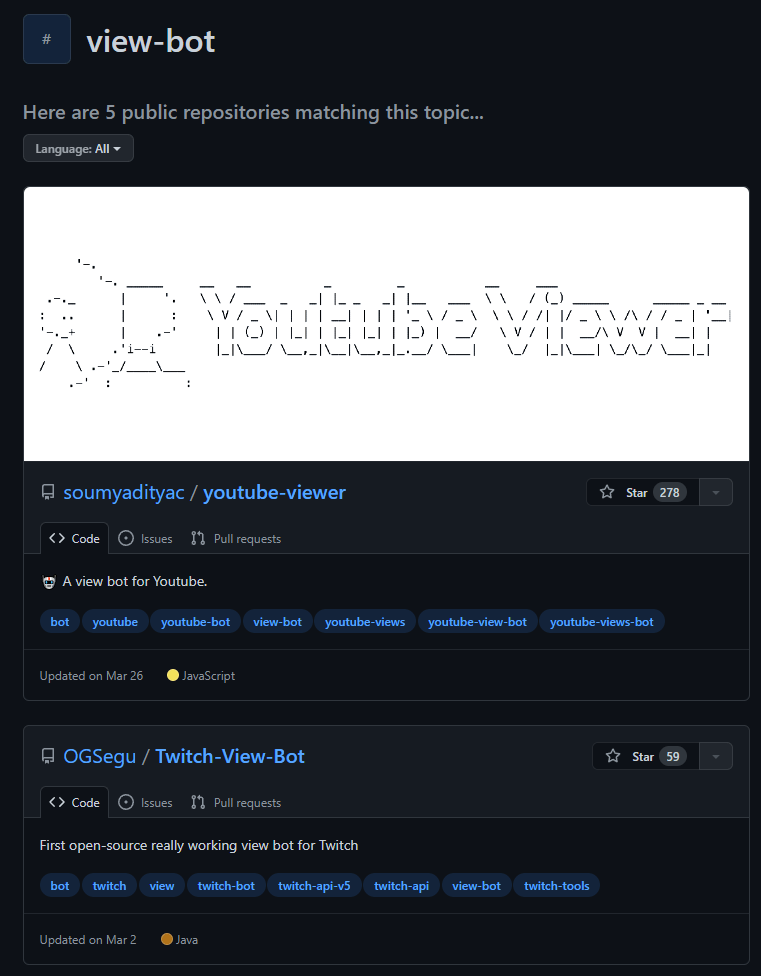
Viewbotting services
For streamers unable or unwilling to create their own view bot scripts, there are dozens of viewbotting services that offer thousands of views for low prices, often with free trials available to entice curious streamers.
Viewbotting services offer thousands of bots that will view your stream for a monthly cost as low as $10. These services offer a higher level of control than rudimentary scripts, such as the capability to add or remove viewers instantly, set viewer join and leave intervals, and choose the region from which “viewers” originate. Using view bot services is against the terms of service of major streaming platforms like Twitch and YouTube.
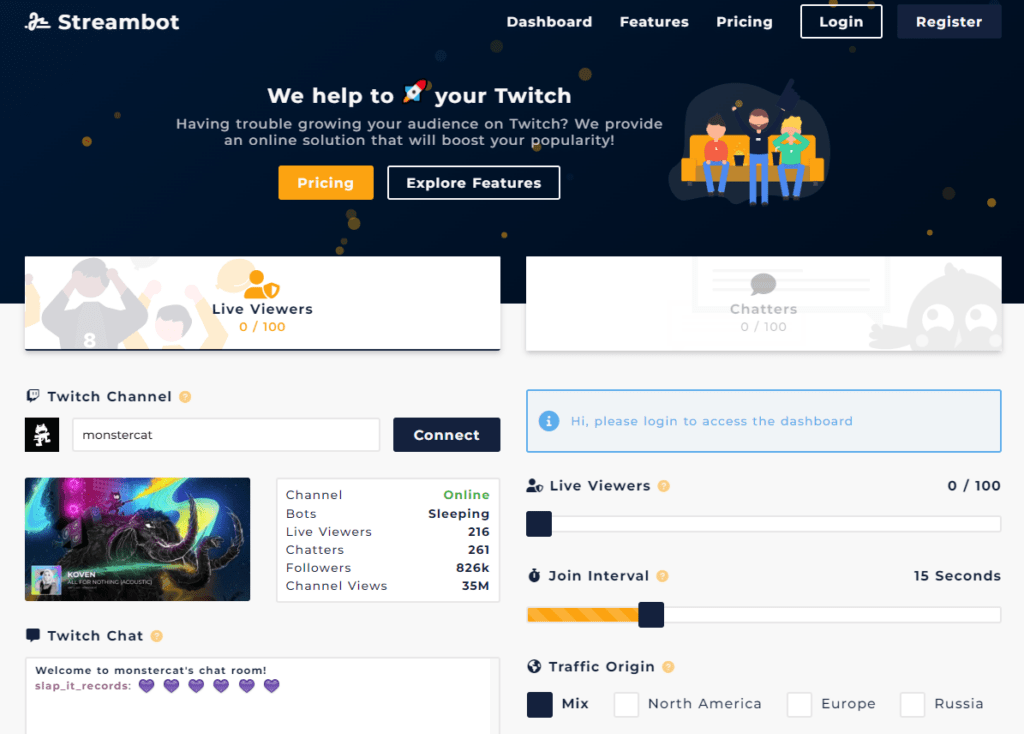
Malicious viewbotting
While not exactly a type of viewbotting, malicious viewbotting is also worth mentioning.
Malicious viewbotting is when people send bots to a stream other than their own, in an attempt to get the streamer banned from Twitch, or simply lower their credibility. This technique is so common that Twitch provides a FAQ for streamers to deal with it.
Malicious viewbotting is unlikely to result in a ban for the targeted streamer, but Twitch recommends reporting instances right away.
Perhaps the largest impact of malicious viewbotting is that it creates an attribution problem for Twitch, which may have difficulty discerning whether a user is viewbotting their own channel, and deserving of a ban, or is the victim of malicious viewbotting.
How to spot view bot use
Spotting unsophisticated viewbotters is not particularly difficult if you know what to look for. Typically, a simple view bot is just that: a bot that views videos. As such, they won’t increase any other metrics, such as engagement, chat activity, or subscriber numbers. If a streamer or content creator routinely gets high viewership numbers with relatively low engagement and subscribership, it’s a fair sign that foul-play could be involved. A formulaic, generic chat with repeated comments like “awesome stream” and “love this” is also a dead giveaway.
How viewbotting hurts go-to-market efforts
Not only is viewbotting a dishonest way to get ahead on streaming platforms and unfair to other streamers who worked hard to build an audience, it also degrades the value of the platform for advertisers.
Like other fake engagement techniques, such as click fraud and lead-gen fraud, viewbotting is a form of Ad Fraud. Essentially, viewbotting steals from advertisers who paid for placement that was ostensibly supposed to reach real humans, not bots.
Under the Twitch Partner Program, high-profile streamers can earn revenue from ads displayed on their channel in the form of a commission for every ad impression. If those impressions are generated by bots, not real people, then the ad budget used to create and place those ads has essentially been wasted.
If it costs $2000 for 100,000 impressions on YouTube, and 15-20% of those impressions are fake, that’s $150-200 wasted. Considering most YouTube advertising campaigns measure impressions in the millions, the costs of those fake impressions can add up fast. Budget is also used faster when it’s wasted on fake impressions, causing brands to potentially miss out on opportunities with genuine customers.
And if advertisers aren’t vigilant in weeding out bot impressions, it’s possible to waste even more budget on remarketing efforts, sending good money after bad bots to retarget “viewers” that never existed in the first place.
But the waste doesn’t end there. False impressions also make their way into advertisers’ data, skewing their metrics and tainting the data used to make further advertising decisions.
Can you block viewbotting?
Unfortunately, since viewbotting takes place on streaming services, such as Twitch and YouTube, it’s up to those services to fight viewbotting and hold fraudsters accountable. Luckily, major streaming platforms are taking the problem very seriously, and have taken steps to ensure quality viewership and punish those who would cheat to get ahead.
Twitch actively monitors for viewbotting, and will indefinitely ban any user caught using view bots to boost their own streams. And though malicious viewbotting complicates this policy, the company has had some success: Twitch banned over 15 million bot accounts last year.
The live-streaming giant has also successfully sued multiple creators of view bots, putting pressure on companies operating in the quasi-legal bot services market.
And while you can’t block viewbotting on the native platform, you can block bot traffic from Google, Facebook, or YouTube campaigns using go-to-market security tools.
The high cost of ad fraud and fake Traffic
This kind of invalid traffic is a far-reaching problem that has grown to affect every corner of the internet and shows no signs of slowing down.
In our recent research report, we found that, on average, 22.3% of unique site visits across all industries are bots. But the gaming industry blew that average out of the water with an astounding 66% invalid traffic rate on unique site visits.
Audience pollution at that level can have major impacts on marketing data, efficiency, and even the bottom line. If 66% of site visitors are bots, then two-thirds of your marketing data is contaminated, and it’s impossible to make good marketing decisions based on bad data.
And beyond wasting time, those fake users, views, and ad clicks have real financial consequences. Advertisers are estimated to lose $68 billion in wasted ad spend by the end of 2022, according to Juniper Research.
Protect Your Pipeline with Go-to-Market Security
Considering that 41% of all web traffic is invalid traffic, when you advertise on any video-based platform–or any web-based platform, for that matter–chances are good that your ads will be exposed to bots (view bots included, of course).
Knowing which impressions or clicks are real potential customers and which are bots, fraudsters, or bad actors is critical to the integrity of your campaigns, data, and go-to-market efforts writ large.
To fight viewbotting and the fake web, marketers need tools that provide end-to-end protection for their go-to-market efforts and customer journey. That’s where CHEQ can help.
CHEQ’s bot mitigation engine uses advanced fingerprinting and multi-layered security models to monitor and block bot activity so you can monitor the authenticity of all traffic entering your funnels and pipelines, whether via paid marketing campaigns, organic search, affiliate programs, or any other method.
With CHEQ, marketers can be confident of the integrity of all data flowing through their advertising audiences, campaign analytics, CRM, DMP, CDP segments, and business intelligence systems, and rest assured that decisions are made on real, solid data.
Within two months of partnering with CHEQ, the UserWay team reduced their unqualified traffic by 56% and redirected their ad spend towards real businesses seeking solutions for digital accessibility.
To learn more and find out what’s real (and what’s not) in your funnel, get started with a demo of CHEQ today.
