Cybersecurity for CMOs: Why smart organizations implement CAS
Kerry Coppinger
|Marketing | September 01, 2021

Historically, cybersecurity has been seen by many as an intimidating industry reserved for a few highly technical and highly specific use cases. Information technology teams have been using cybersecurity tech to avoid any major information leaks, hacks, or data breaches. Meanwhile, other departments within an organization generally tended to stay away from the topic and considered it “someone else’s problem.” However, this way of thinking leads to a variety of business objectives being disrupted. At best, when cybersecurity isn’t considered by all departments, time and resources are mismanaged. At worst, pipeline and revenue opportunities are missed and a mass amount of budget is spent nurturing invalid users.
This is exactly why smart CMOs are already adopting cybersecurity measures to protect their customer acquisition funnels. When bots and fake users interact with marketing assets like advertisements and other digital campaigns, they are taking up space that could be better filled by legitimate users with the intention to become customers. Analytics are also skewed when cybersecurity is not in place because invalid users make up about 40% of the internet and, therefore can find their way onto your site. They pose as real users, but in reality, some have malicious intent, some are robots, and some are hiding their identities behind middle-man tools like proxies. It is abundantly clear that CMOs want to increase their chances of acquiring real customers, but with invalid traffic polluting their efforts, this becomes incredibly difficult. There are several areas where cybersecurity can be beneficial, but for the purpose of this article, we’ll focus on three that typically sit beneath the CMO.
Each team that sits under the CMO can reap the benefits of cybersecurity
Data & Analytics
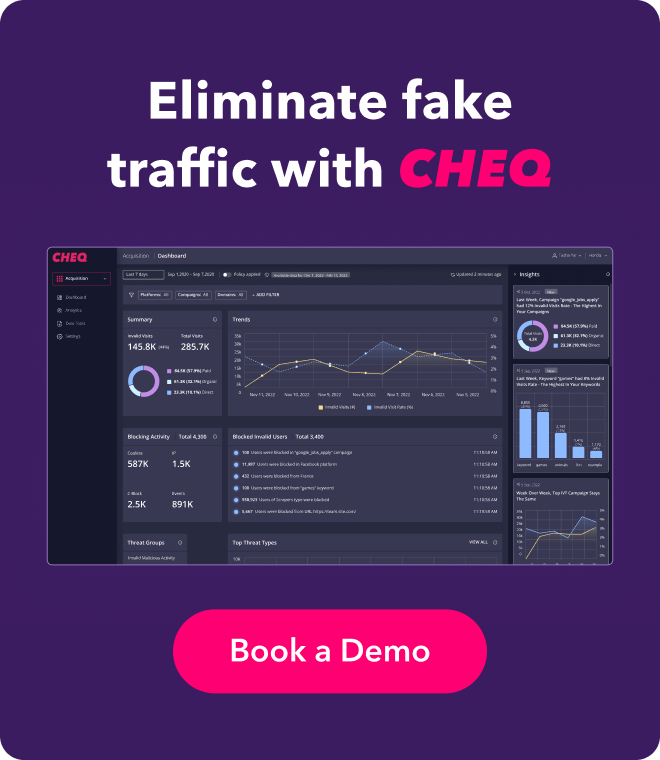
Analytics teams face the challenge of providing accurate and actionable data to the business so precise decisions can be made. However, many business intelligence platforms tend to overlook invalid traffic or incorrectly identify it as real site visitors. As you can imagine, this can snowball and lead to major strategic business choices being made based on bad data. In fact, when looking at just direct traffic, about 37% of it is invalid, or made up of fake users and bots. If invalid users are not filtered out, then this is a major portion of your audience that serves no purpose but to take up space, and cannot ever convert into real paying customers. Business leaders might scratch their heads wondering why the website is not performing as expected, and spend valuable resources and time making changes to assets, when in reality you were adjusting your strategy for invalid users not real human prospects.
Marketing
Marketers continually put out campaigns that target a set list of prospects or an audience, and then those campaigns become optimized toward users that interact with digital assets. When invalid traffic is present, this poses at least 2 major issues. First of all, audiences are frequently polluted with bots and fake users, so you are targeting users that are not legitimate prospects to begin with, which in turn skews the entire campaign. Additionally, when these invalid users continually interact with your campaign assets, your platforms will optimize your campaign toward invalid users and before you know it your campaign will be overrun with these invalid prospects. In order to mitigate these risks, cybersecurity can get ahead of these problems at the start of each campaign and then continually calibrate to ensure the most accurate protection.
Business Development
Business Development teams spend several hours each day trying to engage with prospects who, in many cases, have filled out a form on their website or otherwise showed interest in their services. However, invalid users can make their way into these funnels as well. They fill out forms, request demos, and manipulate funnels in a variety of ways. It is safe to say CMOs and business development leaders want their teams to be using their time in the most efficient ways. But if hours are being spent on nurturing bots and fake users, teams are less effective and productive. Cybersecurity can help teams avoid these problems and ensure time is only being spent on real users that have a chance to convert. This also frequently can lead to increased conversion rates and pipeline and revenue increases as well.
Since each of these areas ultimately contributes to customer acquisition, the overarching strategy they use to mitigate risks has become known as Customer Acquisition Security, or CAS. This term encapsulates the concept that cybersecurity is no longer just an isolated department, but can be adopted in various ways. Strategies like CAS expand the meaning of cybersecurity to cover more departments and become more central to an organization’s overall well-being. CAS is one way that companies can democratize cybersecurity and make it more accessible to all teams. By acknowledging the power cybersecurity has, and using it in a variety of ways, each business can become more protected in all of its endeavors.
If you are interested in learning more about specific CAS solutions, and potentially implementing cybersecurity technology for your customer acquisition or go-to-market teams, CHEQ can help. CHEQ is the leader in Customer Acquisition Security and has helped thousands of customers achieve success through adopting cybersecurity in a variety of ways. Reach out to our team for a demo today.