What is Domain Spoofing and Why is it Still a Problem?
Oli Lynch
|Cyber Risks & Threats | August 05, 2020

Website spoofing, or domain spoofing, is the creation of low-quality websites, often masquerading as well-known or high-quality sites, usually for the purposes of fraud.
Some of the biggest recent ad fraud campaigns have used domain spoofing to devastating effect, and it remains a headache for pay-per-click (PPC) platforms and advertisers.
So, let’s dig into what exactly domain spoofing is and how it works.
Domain Spoofing 101
By passing off low-quality websites as premium inventory, advertisers can host video and display ads and then pass bot traffic through the ads to collect a payout.
It sounds devastatingly effective, and it is.
The advertisers pay out for traffic from this ‘premium’ ad placement but see no conversions as the traffic is fake.
Investigating how to make money with real news and fake sites
In one investigation, Megan Graham, a CNBC reporter, investigated this practice after seeing her recent CNBC article lifted in its entirety. It was one of many stolen articles placed on a (legitimate sounding) news site called “New York Times Post.”
She points out: “It all underscores the fact that the ad tech space is so convoluted, it’s easy to make money from legitimate advertisers just by setting up a web page.” In an experiment, Graham then showed how simple it is to set up a website (with GoDaddy), set up an SSL certificate to avoid setting off Google warning triggers, and set up a new site (she chose “Tribune Times Today”) setting up simple scraping methods to populate the news site.
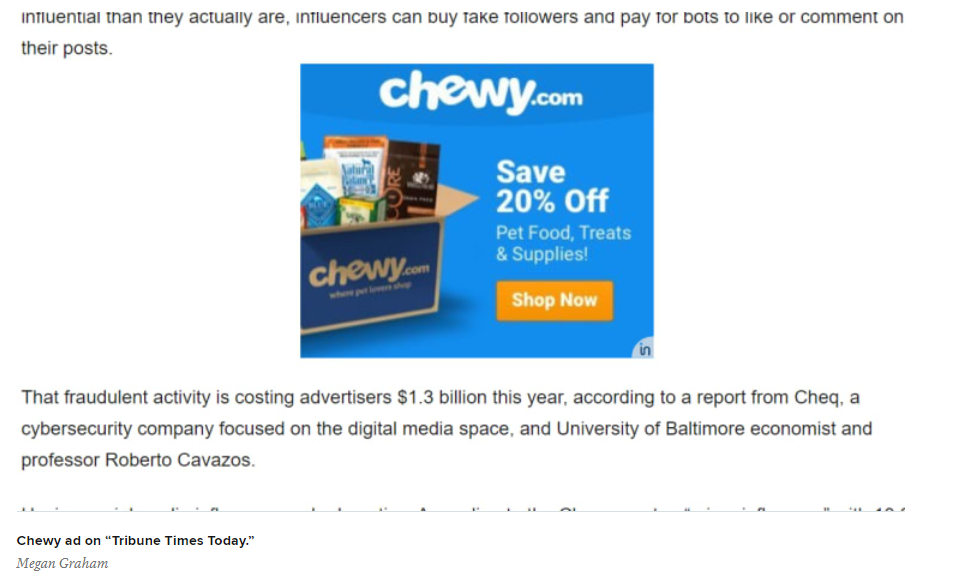
Through a simple process, she applied and received permission to serve ads from a number of AdTech companies on this “news site” (Google AdSense refused permission on the grounds that the Tribune Times “scraped content”). Nevertheless, this simple and easy experiment soon saw ads populated by top brands including Kohl’s, Wayfair, Overstock, and Chewy”. [In a statement, Overstock said that as an advertiser it is negatively impacted by this fraud and does “everything in [its] power to prevent it.”]
In an ultimate act of irony, pet supplies company Chewy.com paid for an ad that appeared on one of Megan’s stories about a major CHEQ report about bad actors and the economic costs of ad fraud (this story appeared on CNBC and was copied on to the spoofed site).
All in all, its domain spoofing is bad news for everyone except fraudsters.
Domain spoofing works in several different ways, which are:
URL Substitution
This is perhaps the simplest way of domain spoofing. The fraudsters hijack the server where the pay-per-click (PPC) auction is hosted by substituting the real URL of a premium site or a fake one.
The advertiser will see that their site has been hosted on a site such as nytimes.com, but in reality, the ad was redirected to a low-grade site at the last moment.
Malware
Using infected apps or browser extensions, often packed with hitbots conducting click spamming, fraudsters can generate a ton of views and clicks on paid ads.
You might have experienced a situation where a website you’ve visited starts trying to download a file via a pop up window. Or, perhaps an app you’re using seems to display random ads at awkward times.
Just some giveaway signals that you’re using ad fraud-enabled malware.
By harnessing the power of malware, fraudsters can inject ads into websites that you’re viewing or into your app without your knowledge. They then generate clicks and collect that sweet, sweet payout.
Cross-domain embedding
This is quite a simple way to spoof websites using iframes. An iframe is an HTML component that allows developers to host content such as videos or other content within a small window on their website.
By embedding other websites or ads within these iframes, it can look like ads are being displayed on another (higher quality) website.
This is also an approach used to display ads from premium vendors on less appealing sites, such as those hosting pornography or hate speech.
Building fake sites and monetizing them
Like the CNBC investigation above, a relatively simple way is to spoof, if not a site itself, then the copyright and investment of legitimate sites, such as CNBC, to monetize your offering and earn a payout. The challenge has grown so large that news sites have opted to put up essentially “do not steal signs”, such as the Midwest Center for Investigative Reporting: “You can’t republish our material wholesale, or automatically; you need to select stories to be republished individually. You can’t use our work to populate a website designed to improve rankings on search engines or solely to gain revenue from network-based advertisements.”
Mix of spoofing, but it all makes money
You’ll notice that there is a mixture of website spoofing approaches in the list above. Some are done on the server; others are done in the browser or via external software, such as malware infections.
In terms of server-side infections, as seen in hugely successful ad fraud operations like MethBot and HyphBot, this involves compromising the ad exchange or SSP.
Spoofers can often infiltrate these servers with spoofed or compromised IP addresses or by using their own servers to send fake data disguised as the real deal. The way it works is that a buyer may see the URL for reputablewebsite.com (be it CNN or Huffington Post or any number of sites out there) but, in reality, is buying from a completely unrelated site. The “Methbot” scheme, for instance, spoofed more than 6,000 premium publishers in the U.S. and generated as much as $5 million in fraudulent revenue per day.
In recent years, app malware and infected web browsers have become increasingly sophisticated and effective at both spoofing domains and generating clicks. In 2020, we saw Tekya, a form of malware that uses click injection to click on embedded and spoofed ads.
Why is website spoofing still a problem in 2023?
Very simply: Money.
For ad fraud operators, spoofing premium inventory is the fastest way to get paid. So, they will always be looking at ways to get around whatever security is put in place.
The Financial Times was hit by domain spoofing of its trusted brand, with the publisher estimating the value of a fraudulent inventory across 10 ad exchanges to be $1.3 million
a month. Decrying the incident, Anthony Hitchings, the FT’s digital advertising operations director said: “The scale of the fraud we found is jaw-dropping. The industry continues to waste marketing budgets on what is essentially organized crime.”
Although things are being done in an attempt to stamp out website spoofing and ad fraud, it still looks like we’re a long way from the promised land.
Advertisers can minimize their exposure to the damages of ad fraud and website spoofing by using click fraud prevention software. CHEQ offers the most comprehensive protection against these sneaky fraudulent practices, with coverage across the most popular PPC platforms and networks.
P.S.
Want to protect your sites and ads? Click here to Request a Demo.